Aws Waf
Now I want to restrict access to my app to an IP range, so in comes WAF I configured WAF to deny all traffic and a rule to allow if IP is in range When accessed from outside the allow range, cloudfront responds by returning the 403 response, which is /indexhtml and http0 articles and tools covering Amazon Web Services (AWS), including.

Aws waf. AWS WAF Security Automations A solution that contains all AWS WAF samples developed so far wafreactiveblacklist, wafbadbotblocking, wafblockbadbehaving and wafreputationlists For the full solution overview visit AWS WAF Security Automations File Structure. Now I want to restrict access to my app to an IP range, so in comes WAF I configured WAF to deny all traffic and a rule to allow if IP is in range When accessed from outside the allow range, cloudfront responds by returning the 403 response, which is /indexhtml and http0 articles and tools covering Amazon Web Services (AWS), including. AWS WAF and AWS Shield help protect your AWS resources from web exploits and DDoS attacks AWS WAF is a web application firewall service that helps protect your web apps from common exploits that could affect app availability, compromise security, or consume excessive resources.
Harnessing the full power of the AWS® cloud involves far more than building a solid technical infrastructure Amazon developed the WellArchitected Framework (WAF) to enable companies to build the most operationally excellent, secure, reliable, efficiently highperforming, and costoptimized infrastructure possible for their businesses This post addresses the second pillar, security. I would rate AWS WAF a seven out of ten It does what it is supposed to do, probably not in the best way and not in the best UI, but it works We like the pricing part, but management is the thing that we don't love the most If things keep improving, we're definitely going to scale with AWS WAF. AWS WellArchitected Labs > Security > 0 Level Intermediate Labs > Level 0 Automated Deployment of Web Application Firewall > Configure AWS WAF Configure AWS WAF Using AWS CloudFormation , we are going to deploy a basic example AWS WAF configuration for use with CloudFront.
Uses the builtin AWS WAF injection match statement to inspect the request URI path for patterns that match malicious SQL code Linux operating system VendorName AWS, Name AWSManagedRulesLinuxRuleSet, WCU 0. 0 Why does AWS Security group not allow inbound http traffic by sgID 2 How to whilelist specific IP addresses from AWS WAF 2. Currently AWS WAF v2 is supported in master branch and >= v0 includes functionality only for AWS WAF v2 If you need the script to work with AWS WAF v1, please check the tag v100 fail2banawswafv2.
The AWS WAF console guides you through the process of configuring AWS WAF to block or allow web requests based on conditions that you specify, such as the IP addresses that the requests originate from or values in the requests In this step, you create a web ACL To create a web ACL. AWS WAF is a web application firewall that helps protect your web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources;. AWS WAF is a web application firewall that helps protect your web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources AWS WAF gives you control over which traffic to allow or block to your web applications by defining customizable web security rules.
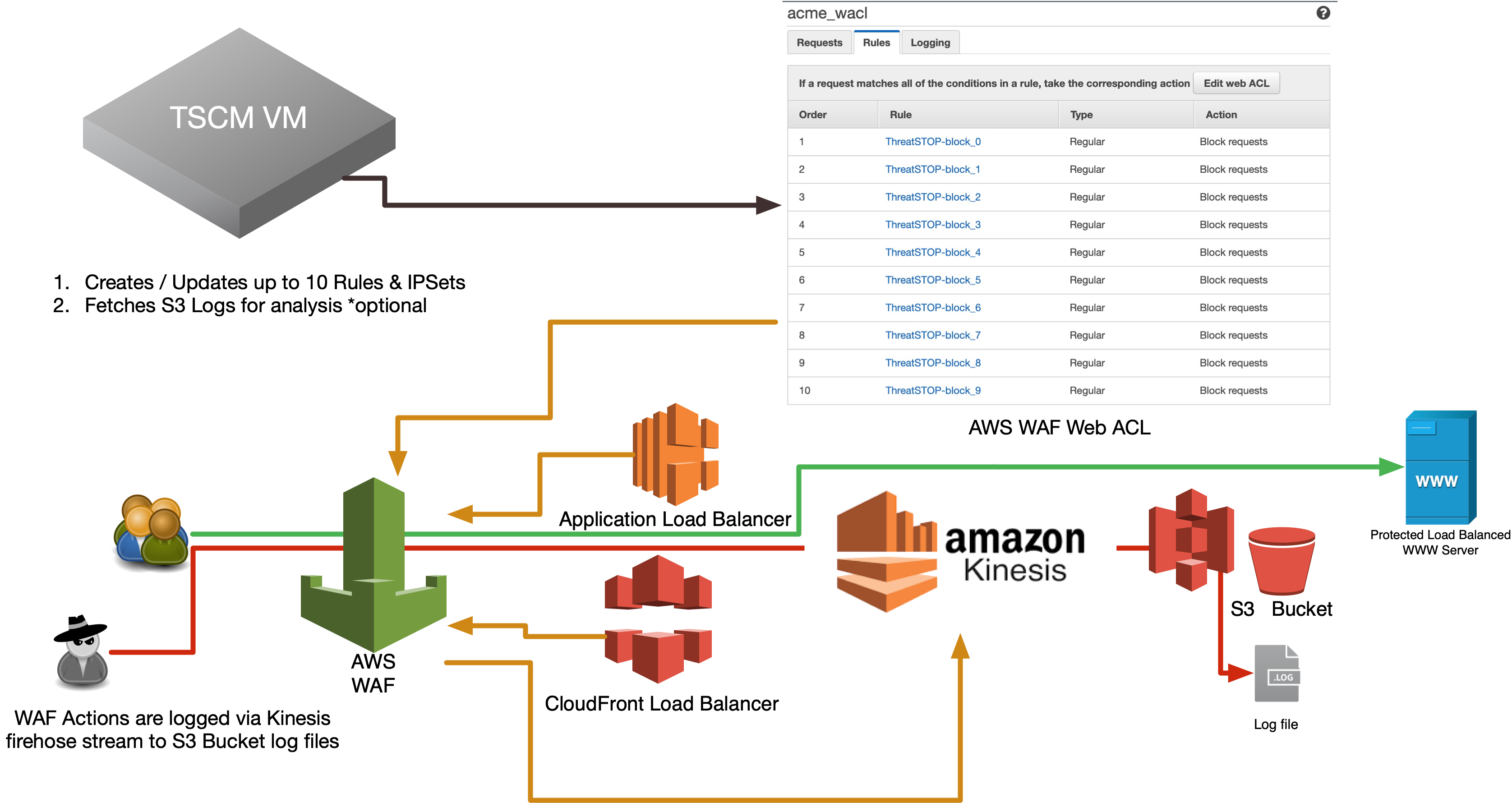
Protect Your AWS Cloud Environment from Hackers ThreatSTOP can turn your AWS WAF into threat intelligence, highsecurity powerhouse and do it with a simple Cloud service Choose policy and integrate policy with Amazon's WAF and see reporting about threats that are being blocked Compatible with AWS WAF and AWS Classic. 22 Linking Kinesis Firehose to AWS WAF From here on, we will link Kinesis Firehose to AWS WAF By doing this, it is possible to save the request log that until now was able to acquire only part of log data up to 3 hours ago to S3 Select “WAF & Shield” from the service Choose "Go to AWS WAF" Choose "Web ACLs" from the side bar. AWS WAF is a web application firewall that helps protect web applications from attacks by allowing rules configuration that allow, block, or monitor (count) web requests based on defined conditions AWS WAF helps protects from common attack techniques like SQL injection and CrossSite Scripting (XSS), Conditions based include IP addresses, HTTP.
Blocking IP's using AWS WAF so that only users connected to a VPN can access CloudFront 0 AWS WAF Pricing For Blocked Requests?. AWS WAF is a web application firewall (WAF) you can use to help protect your web applications from common web exploits that can affect application availability, compromise security, or consume excessive resources3 With AWS WAF, you can allow or block requests to your web applications by defining customizable web security rules. Step 3 Creating the AWS WAF (Web Application Firewall) Step 3a Go the AWS WAF Management Console and click on “Configure web ACL” The AWS WAF overview is shown Here is the hierarchy of AWS WAF Web ACL has a bunch of Rules and Rules have a bunch of Conditions which we would be creating in the subsequent steps Click on Next.
AWS WAF is a web application firewall that helps protect your web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources AWS WAF gives you control over which traffic to allow or block to your web applications by defining customizable web security rules. AWS WAF is a web application firewall (WAF) that helps you protect your websites and web applications against various attack vectors at the application layer (OSI Layer 7) This whitepaper outlines current recommendations for implementing AWS WAF to protect existing and new web applications This paper applies to anyone who is tasked. With AWS WAF, you can create security rules to block common attack patterns You can centrally automate and simplify AWS WAF rules using AWS Firewall Manager AWS Shield Advanced is a comprehensive application security suite that tailors detection based on your application traffic patterns, provides detailed attack reporting, and gives access.
Map of Lists to List The second approach it to update the format in my ipwhitelist module IP addresses are now written in the aws_waf_ipset format, aka as a list of maps The only missing part we need the opposite conversion to implement cidr output value We need to convert that list of maps back to a plain list of CIDR blocks (for Security Groups). With AWS WAF, you can create security rules to block common attack patterns You can centrally automate and simplify AWS WAF rules using AWS Firewall Manager AWS Shield Advanced is a comprehensive application security suite that tailors detection based on your application traffic patterns, provides detailed attack reporting, and gives access. About AWS WAF AWS WAF is a web application firewall that helps protect your web applications or APIs against common web exploits that may affect availability, compromise security, or consume excessive resources.
FortiWeb Cloud WAFasaService on Amazon Web Services (AWS) allows organizations to rapidly deploy web applications while providing bestinclass security for missioncritical applications – protecting applications and APIs from threats and addressing compliance requirements Organizations protecting their web applications with this Software. With AWS WAF, you can now deploy AWS Managed Rules, which gives you protection against common vulnerabilities and emerging threats In this tech talk, we will demonstrate how you can leverage AWS. Protect Your AWS Cloud Environment from Hackers ThreatSTOP can turn your AWS WAF into threat intelligence, highsecurity powerhouse and do it with a simple Cloud service Choose policy and integrate policy with Amazon's WAF and see reporting about threats that are being blocked Compatible with AWS WAF and AWS Classic.
AWS WAF includes a fullfeatured API that you can use to automate the creation, deployment, and maintenance of security rules With AWS WAF, you pay only for what you use The pricing is based on how many rules you deploy and how many web requests your application receives There are no upfront commitments. AWS WAF is a web application firewall that lets you monitor the HTTP and HTTPS requests that are forwarded to Amazon CloudFront, an Amazon API Gateway REST API, an Application Load Balancer, or an AWS AppSync GraphQL API AWS WAF also lets you control access to your content. Using CloudFormation customers can automate the deployment of their WAF on the AWS cloud You will play a lead role on the team and influence how we design, develop, build, deploy and support AWS WAF.
Blocking IP's using AWS WAF so that only users connected to a VPN can access CloudFront 0 AWS WAF Pricing For Blocked Requests?. CloudFlare The Web Performance & Security Company Cloudflare speeds up and protects millions of websites, APIs, SaaS services, and other. For example, if an IPSet includes the IP address , AWS WAF will allow or block requests based on that IP address If set to true, AWS WAF will allow, block, or count requests based on all IP addresses except data_id (Required) A unique identifier for a predicate in the rule, such as Byte Match Set ID or IPSet ID.
AWS WAF is a web application firewall which protects web applications from threats which could compromise their security or consume resources The solution itself is straight forward and easy to use. AWS WAF is a web application firewall that helps detect and block malicious web requests targeted at your web application Search Forum Advanced search options Forum Announcements How to Use AWS WAF to Mitigate the Impact of CVE Posted by venkat@aws Mar 17, 17 929 PM. About AWS WAF AWS WAF is a web application firewall that helps protect your web applications or APIs against common web exploits that may affect availability, compromise security, or consume excessive resources.
AWS WAF is a web application firewall that enables customers to quickly create custom, applicationspecific rules that block common attack patterns that can affect application availability, compromise security, or consume excessive resources. 0 Why does AWS Security group not allow inbound http traffic by sgID 2 How to whilelist specific IP addresses from AWS WAF 2. Protect Your AWS Cloud Environment from Hackers ThreatSTOP can turn your AWS WAF into threat intelligence, highsecurity powerhouse and do it with a simple Cloud service Choose policy and integrate policy with Amazon's WAF and see reporting about threats that are being blocked Compatible with AWS WAF and AWS Classic.
Amazon Web Services (AWS) is a solid toptier cloud service provider by anyone’s standard, which should make its WAF awfully tempting for both existing customers and those without an AWS presence. Just make sure you have someone who is knowledgeable in AWS to configure and administer your WAF AWS WAF Alternatives If you’re looking to move away from the AWS platform, check out our shortlist of competitive AWS WAF alternatives Be sure to check out our updated post on the best WAFs. Seconds later it was clear that out of this four payloads there is a one lucky winner, which allows for AWS WAF bypass and script execution in the web browser AWS WAF bypass and script execution.
Blocking IP's using AWS WAF so that only users connected to a VPN can access CloudFront 0 AWS WAF Pricing For Blocked Requests?. I would rate AWS WAF a seven out of ten It does what it is supposed to do, probably not in the best way and not in the best UI, but it works We like the pricing part, but management is the thing that we don't love the most If things keep improving, we're definitely going to scale with AWS WAF. For example, if an IPSet includes the IP address , AWS WAF will allow or block requests based on that IP address If set to true, AWS WAF will allow, block, or count requests based on all IP addresses except data_id (Required) A unique identifier for a predicate in the rule, such as Byte Match Set ID or IPSet ID.
Trustwave WAF virtual appliances for Amazon Web Services (AWS) and Microsoft Azure can be deployed as sensors, managers or standalone appliances Virtual Appliance With virtual appliances (VMware ESX/ESXi servers), you can use the hardware of your choice, and help reduce costs and effort in aligning with your organization’s data center strategy. AWS WAF is a web application firewall that helps protect your web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources. AWS WAF is a web application firewall that lets you monitor the HTTP and HTTPS requests that are forwarded to an Amazon CloudFront distribution, an Amazon API Gateway REST API, an Application Load Balancer, or an AWS AppSync GraphQL API AWS WAF also lets you control access to your content.
The AWS WAF is a layer seven firewall that can be enabled to protect a Cloudfront distribution, an Application Load Balancer (ALB), or the API Gateway The function of a firewall is to allow or. For more information, see "Output Full Log of AWS WAF to S3" Analyze incoming traffic using the full logging feature and look for unexpected behavior within the rule group Step2 Identifying the "ruleId" of the unwanted rule from the log Use the AWS WAF logs to identify the IDs of the rules that you want to exclude. Step 3 Creating the AWS WAF (Web Application Firewall) Step 3a Go the AWS WAF Management Console and click on “Configure web ACL” The AWS WAF overview is shown Here is the hierarchy of AWS.
Figure 1 — WAF Filtering and Monitoring HTTP requests Web ACL When WAF associating any of the above three AWS services, it associates with a Web ACL A Web ACL is a fundamental component of WAF. Designed to protect web applications, AWS WAF is a cloud firewall that can be customized to match the needs of an organization, which means you can add and customize security rules for the. 22 Linking Kinesis Firehose to AWS WAF From here on, we will link Kinesis Firehose to AWS WAF By doing this, it is possible to save the request log that until now was able to acquire only part of log data up to 3 hours ago to S3 Select “WAF & Shield” from the service Choose "Go to AWS WAF" Choose "Web ACLs" from the side bar.
The AWS Cloud spans 77 Availability Zones within 24 geographic regions around the world, with announced plans for 18 more Availability Zones and 6 more AWS Regions in Australia, India, Indonesia, Japan, Spain, and Switzerland. AWS WAF is a web application firewall (WAF) you can use to help protect your web applications from common web exploits that can affect application availability, compromise security, or consume excessive resources3 With AWS WAF, you can allow or block requests to your web applications by defining customizable web security rules. AWS WAF is a truly valuable programming when actualized at the departmental level It permits the foundation of the applications that are being executed to be secured in a basic manner since the client can set up rules to stop the weaknesses that can cause a glitch in such applications.
AWS WAF is a web application firewall that helps protect your web applications or APIs against common web exploits that may affect availability, compromise security, or consume excessive resources AWS WAF gives you control over how traffic reaches your applications by enabling you to create. AWS WAF Security Automations is a solution that automatically deploys a single web access control list (web ACL) with a set of AWS WAF rules designed to filter common webbased attacks The solution supports log analysis using Amazon Athena and AWS WAF full logs Conditions, Rules, and Web ACLs. AWS WAF is a web application firewall that helps detect and block malicious web requests targeted at your web application Search Forum Advanced search options Forum Announcements How to Use AWS WAF to Mitigate the Impact of CVE Posted by venkat@aws Mar 17, 17 929 PM.
Now I want to restrict access to my app to an IP range, so in comes WAF I configured WAF to deny all traffic and a rule to allow if IP is in range When accessed from outside the allow range, cloudfront responds by returning the 403 response, which is /indexhtml and http0 articles and tools covering Amazon Web Services (AWS), including. The purpose of this addon is to provide value to your AWS Web Application Firewall (WAF) logs This is done by making the logs CIM compliant, adding tagging for Enterprise Security data models, and other knowledge objects to make searching and visualizing this data easy. Full security without the compromise Web Application Firewalls (WAFs) are critical to protecting your workloads running on AWS To offload the cost and complexity of managing WAF instances in the cloud, our WAFasaService solution combines more than a decade of threat protection with an easytoconsume softwareasaservice model.
AWS WAF is a great option;. 0 Why does AWS Security group not allow inbound http traffic by sgID 2 How to whilelist specific IP addresses from AWS WAF 2. With AWS WAF, you can create security rules to block common attack patterns You can centrally automate and simplify AWS WAF rules using AWS Firewall Manager AWS Shield Advanced is a comprehensive application security suite that tailors detection based on your application traffic patterns, provides detailed attack reporting, and gives access.
AWS WAF is a web application firewall that helps protect web applications from attacks by allowing rules configuration that allow, block, or monitor (count) web requests based on defined conditions AWS WAF helps protects from common attack techniques like SQL injection and CrossSite Scripting (XSS), Conditions based include IP addresses, HTTP.

Amazon Api Gateway Adds Support For Aws Waf Aws Compute Blog

What Is Aws Waf Web Application Firewall Tutorial Links
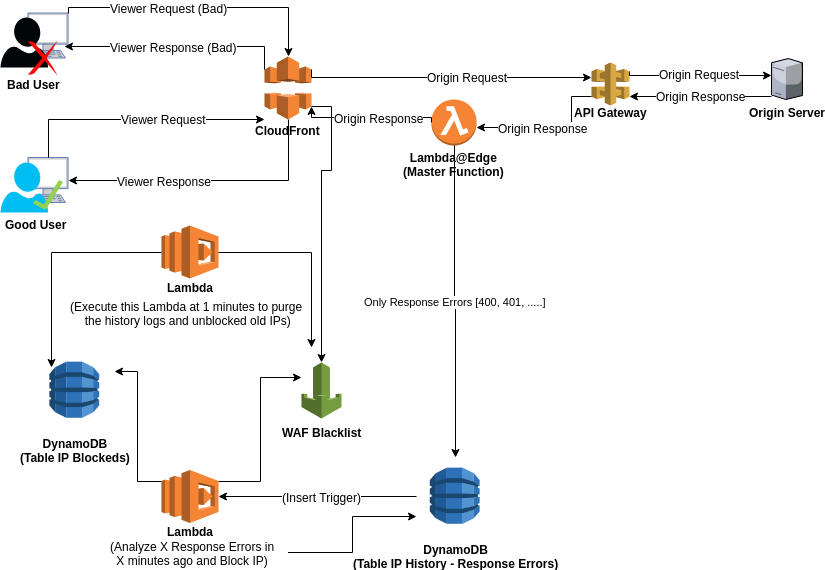
Instant Block Of Attacks To Aws Websites Using Cloudfront Lambda Edge Dynamodb Waf By Hugo Branquinho De Carvalho Conta Azul Engineering Blog
Aws Waf のギャラリー

Web Application Security Using Aws Waf And Aws Shield By Synerzip Medium
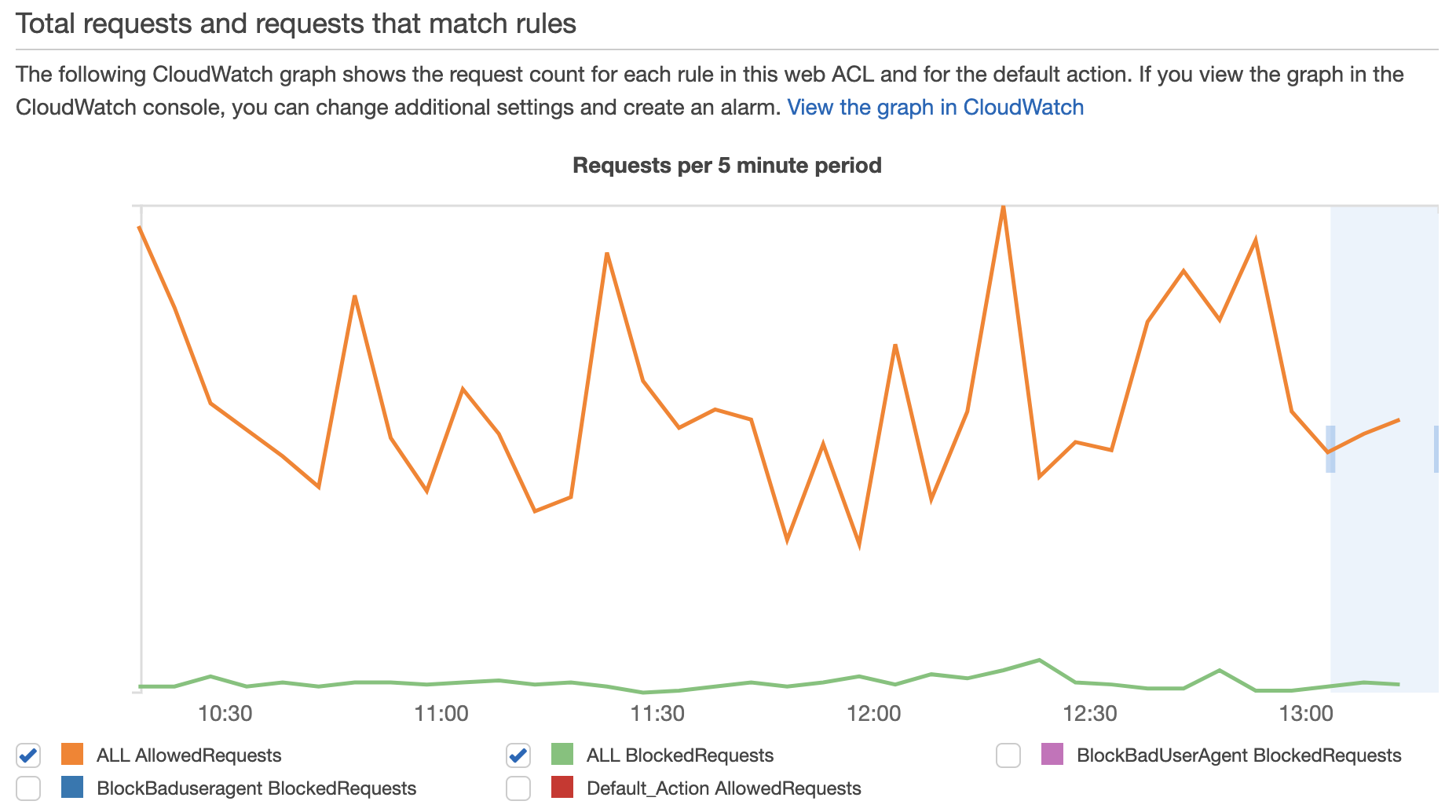
Protect Your Application By Aws Waf The First Cry Of Atom

Waf Sandwich Cloudaxis

Generating Amazon Web Services Waf Rules From Netsparker Standard Netsparker

Aws Waf And Deep Security
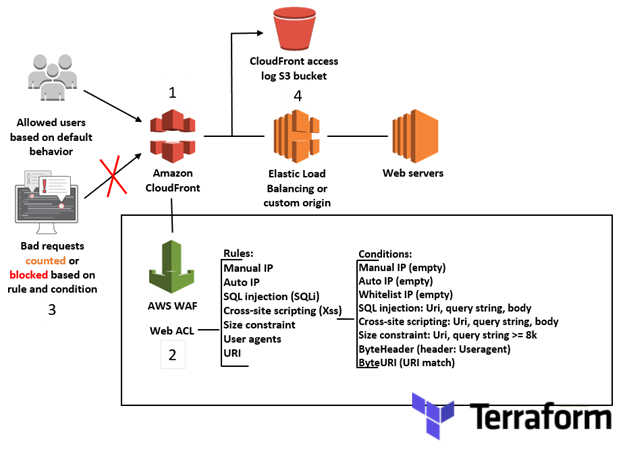
Github Binbashar Terraform Aws Waf Owasp Aws Waf At Terraform Modules To Mitigate Owasp S Top 10 Web Application Vulnerabilities

Deploy A Dashboard For Aws Waf With Minimal Effort Aws Security Blog

Nclouds Blog Secure Web Applications With Aws Web Application Firewall

Deploy Nginx Ingress And Retain Full Control Of Your Aws Load Balancer Steve Horsfield

Wafcharm Provided By Cyber Security Cloud Becomes The No 1 Aws Waf Automation Service In Japan With The Largest No Of Users For An Aws Waf Automated Operation Service Cyber Security

Protect Wordpress Login Using Aws Waf Web Application Firewall To The New Blog

Aws October 15 Webinar Series Essentials Introducing Aws Waf Youtube

Globenet International

Sec323 New Securing Web Applications With Aws Waf

How To Use Aws Waf To Filter Incoming Traffic From Embargoed Countries Aws Security Blog

Nclouds Blog Secure Web Applications With Aws Web Application Firewall
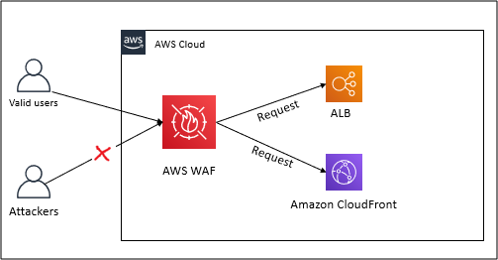
Prominent Aws Security Services Cloudthat S Blog
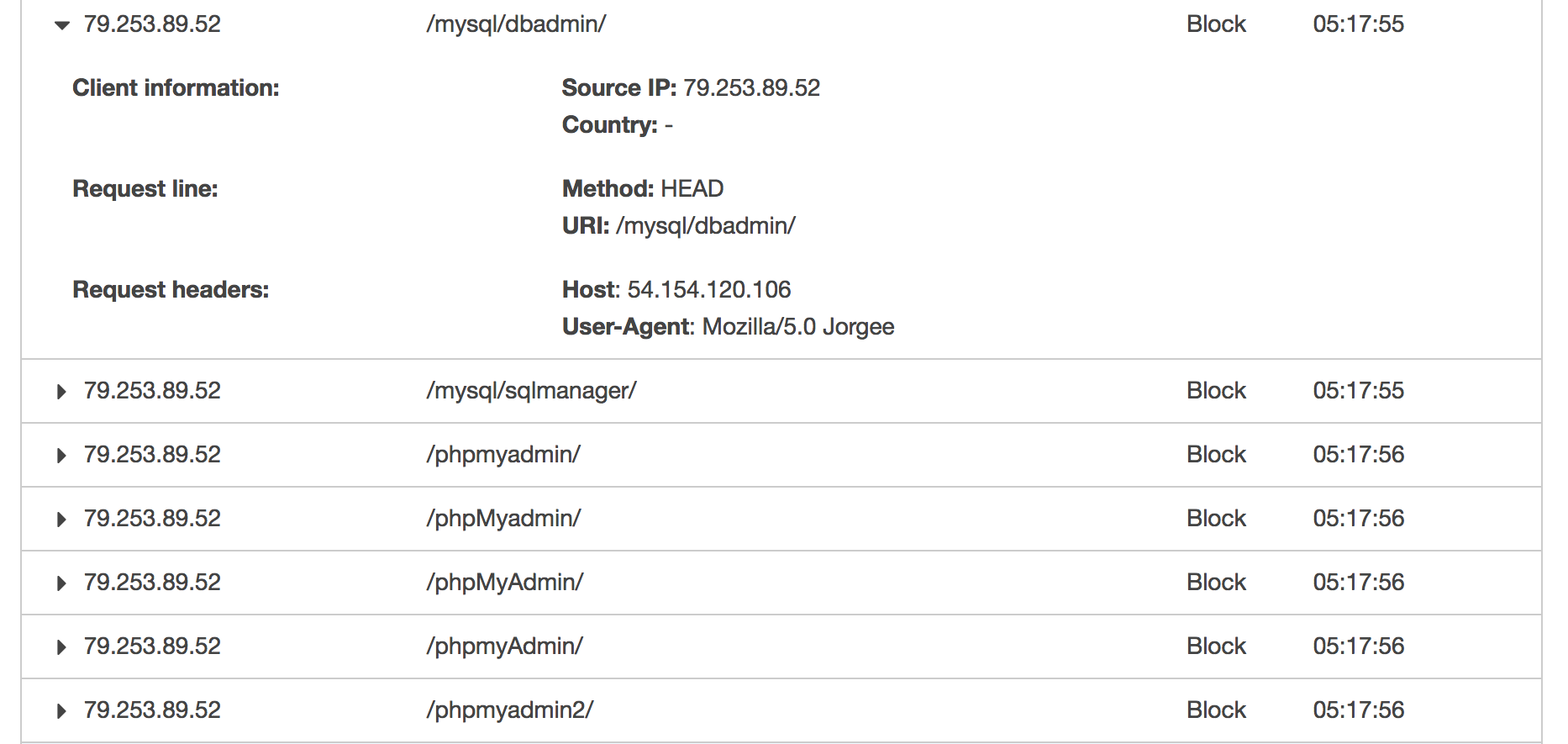
Use Aws Waf To Block Bots Like Mozilla 5 0 Jorgee

Setting Up A Web Application Firewall In Aws Leron Zinatullin S Blog

How To Use Aws Waf To Filter Incoming Traffic From Embargoed Countries Aws Security Blog
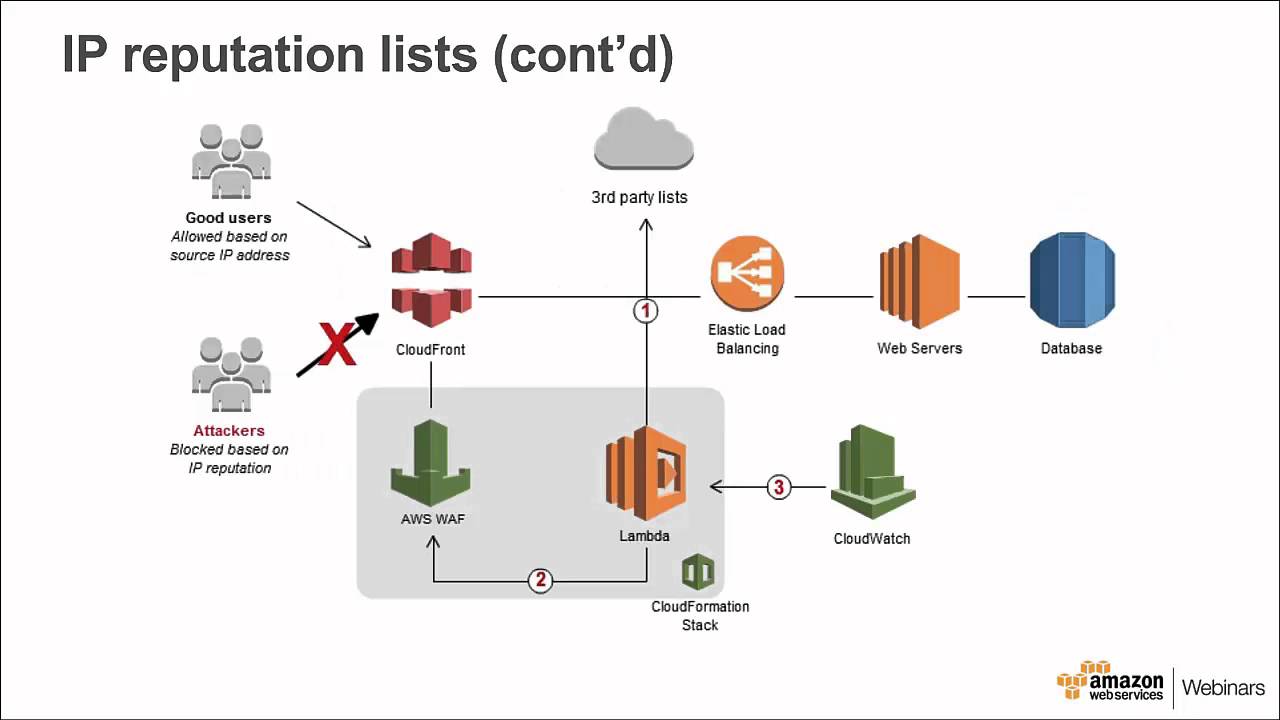
Using Aws Waf And Lambda For Automatic Protection Youtube
How To Get Aws Waf Sample Logs And Full Logging Wafcharm Service For Automation Of Aws Waf Rules Using Ai
Creating Waf Acl In Aws Firewall Manager Vembu Com

What Is The Aws Waf Accolade Partners

Aws Waf And Deep Security

Aws Waf Reviews Pros Cons Companies Using Aws Waf

Secure Cloudfront Distributions With Aws Waf

Q Tbn And9gct Nqkczw481jso25jy7oewrg8tuop06hlq3njf5lesefkkchid Usqp Cau

Get The Last Waf With Aws Web Application Firewall Trinimbus
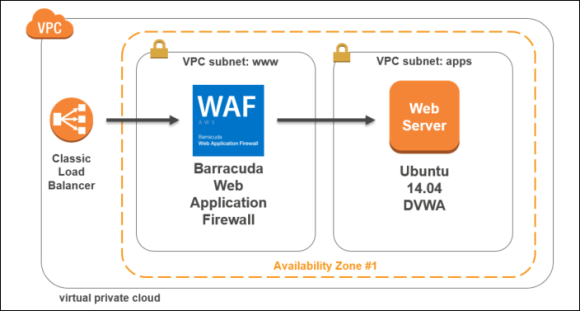
Deploy And Secure An Internet Facing Application With The Barracuda Web Application Firewall In Amazon Web Services Barracuda Campus

11 Web Application Firewall To Compare For Securing Your Online Business
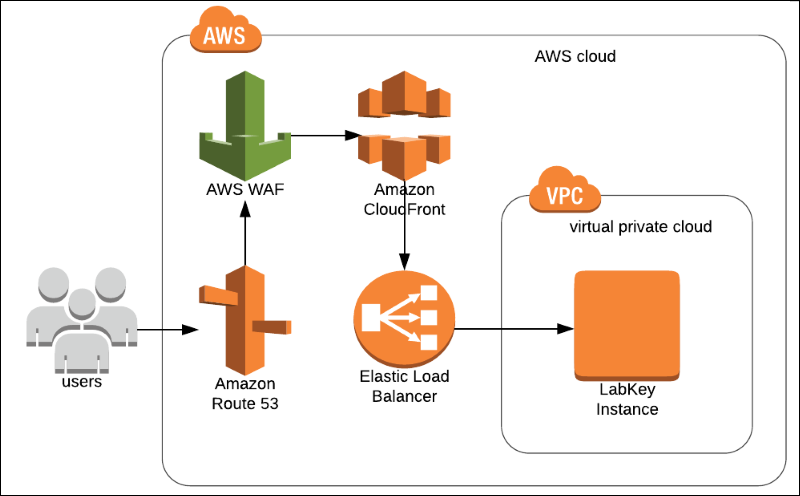
Deploying An Aws Web Application Firewall Documentation

Aws Web Application Firewall Waf Certification

Aws Re Invent 16 Workshop Secure Your Web Application With Aws Wa

Deploy The Dashboard For Aws Waf With Reduced Effort One Stop It Service Provider

Origin Protection With Aws Waf Shield
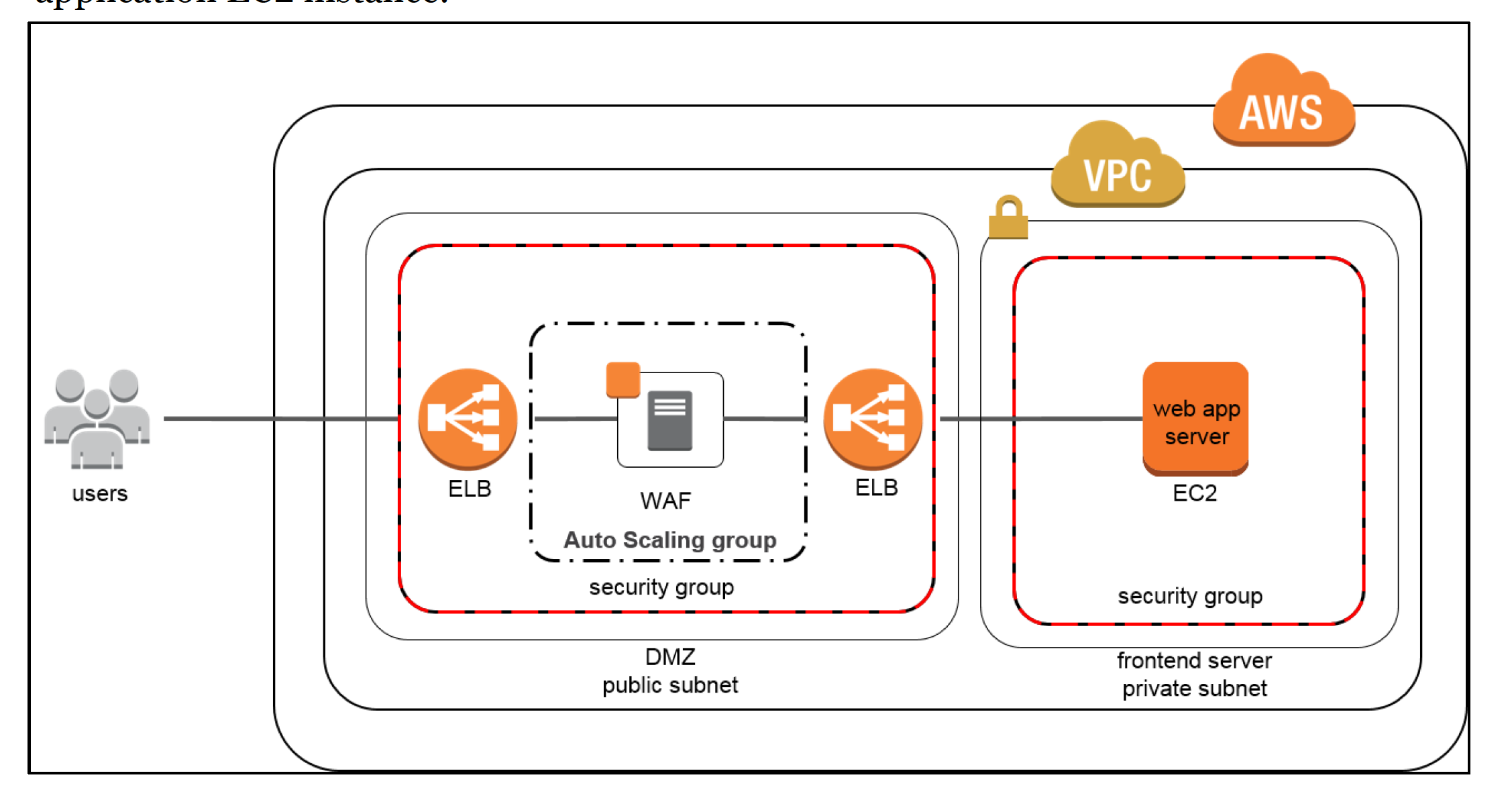
Aws Web Application Firewall Waf Certification

Defense In Depth Using Aws Managed Rules For Aws Waf Part 1 Aws Security Blog

Protecting Your Api Using Amazon Api Gateway And Aws Waf Part 2 Amazon Web Services Computer Parts And Components Solution Architect Gateway
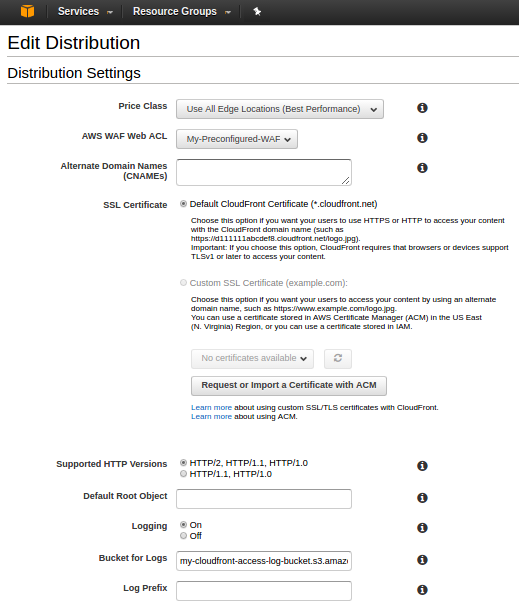
Aws Waf Web Application Firewall With Preconfigured Cloudformation Template And Web Acl For Cloudfront Distribution

Automatically Updating Aws Waf Rule In Real Time Using Amazon Eventbridge Aws Security Blog

Deploying Aws S Web Application Firewall On Cloudfront With Dynamic Content From An Elastic Beanstalk Rails App By Chris Kirk Primer Engineering Medium

Remediate Phase Protecting Workloads On Aws From The Instance To The Edge
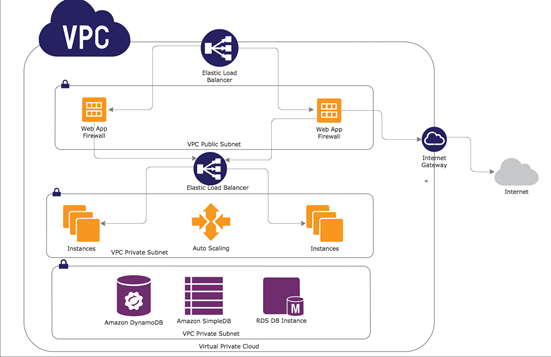
Intrusion Detection Intrusion Prevention And Web Application Firewalls Stackarmor

Aws Waf Web Application Firewall Amazon Web Services Aws

Aws Waf Security Automations Aws Solutions

Getting Started With F5 Web Exploits Owasp Rules For Aws Waf

Amazon Api Gateway Adds Support For Aws Waf Noise
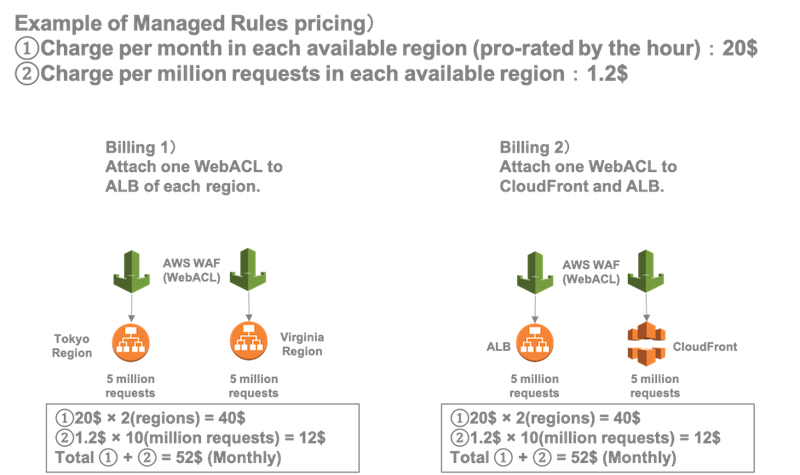
Introduction To Aws Waf Managed Rules Wafcharm Service For Automation Of Aws Waf Rules Using Ai

Aws Waf Introduction And Live Demo Pop Up Loft Tel Aviv

Getting Started With Waf Aws Administration The Definitive Guide Second Edition

Aws Waf Full Review The Best Alternatives 21 Paid Free

What Is The Aws Waf Accolade Partners
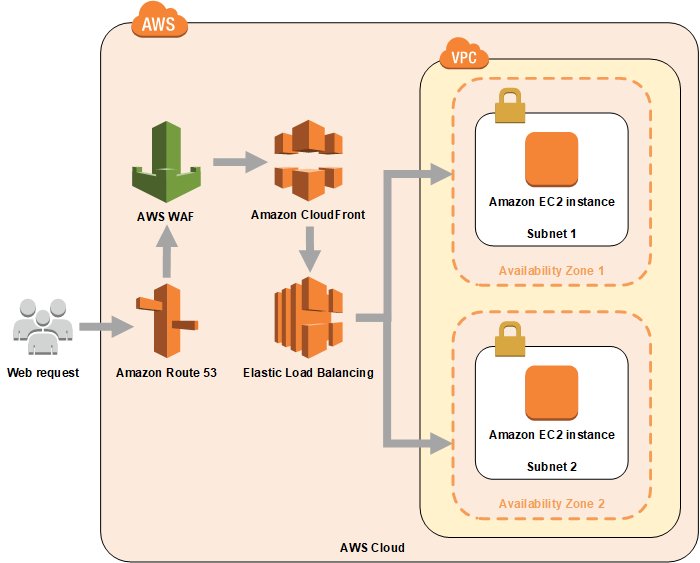
Aws Security Use This New Aws Waf Tutorial To Implement A Ddos Resistant Website T Co Xpt5ch2vn1
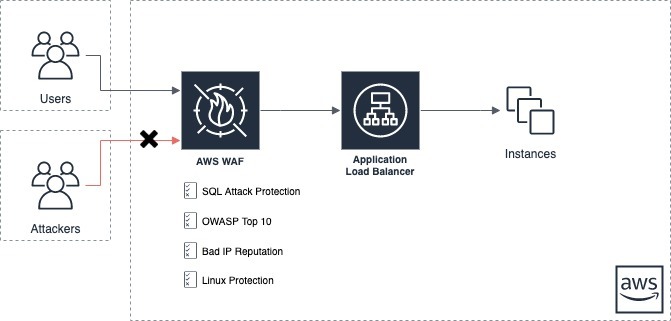
Web Application Protection On Aws Sufle
Configuring Aws Web Application Firewall Kloud Blog
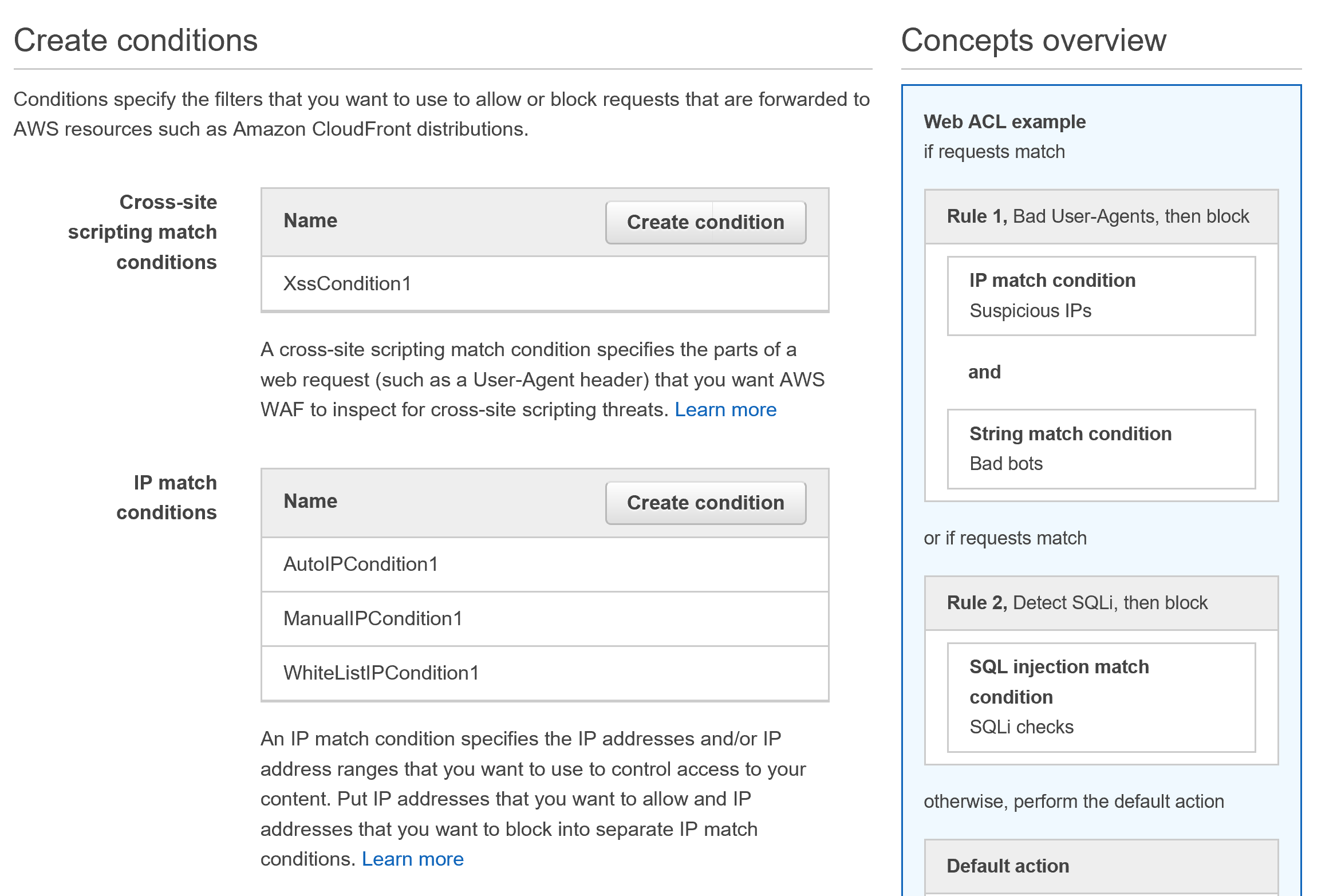
Aws Web Application Firewall Waf Classic Threatstop Dochub

Protect Your Application By Aws Waf The First Cry Of Atom

Q Tbn And9gcqhty94olhrmx Xs1ngnrubiwb6wjb5piek Abjtc4hgwcty11m Usqp Cau

Aws Shield Vs Aws Waf What Are The Differences
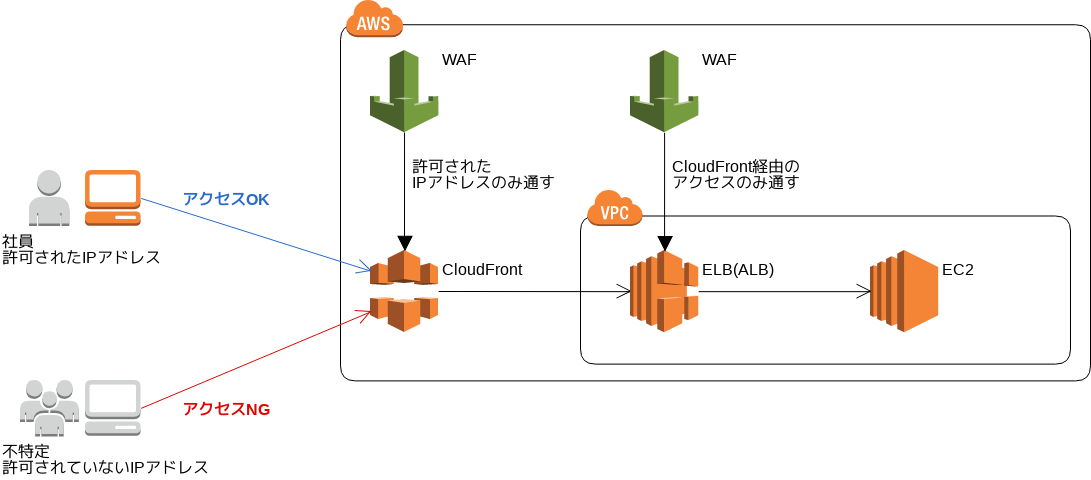
Aws Wafを使って接続できるipアドレスを制限してみた Developersio

Amazon Api Gateway Adds Support For Aws Waf Aws Compute Blog
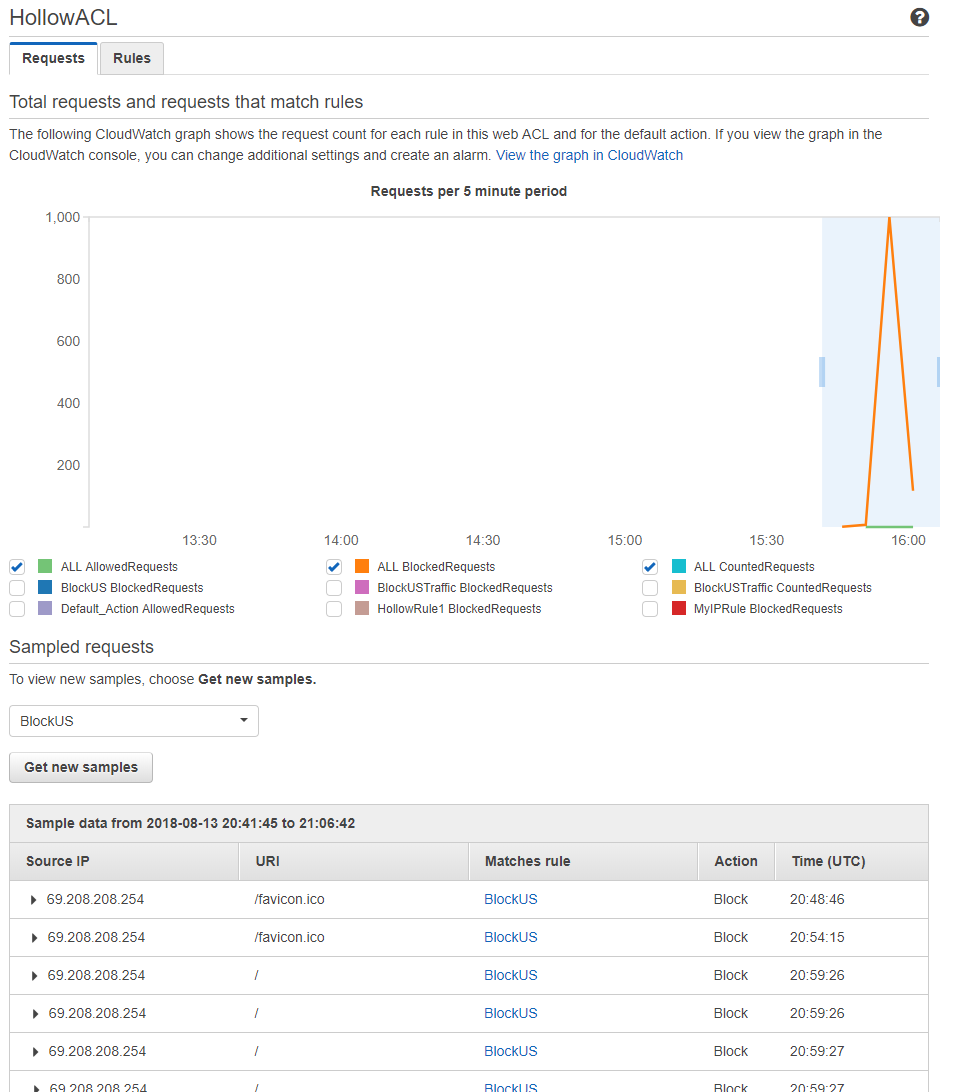
Add Aws Web Application Firewall To Protect Your Apps The It Hollow

Analyzing Aws Waf Logs With Amazon Es Amazon Athena And Amazon Quicksight Noise
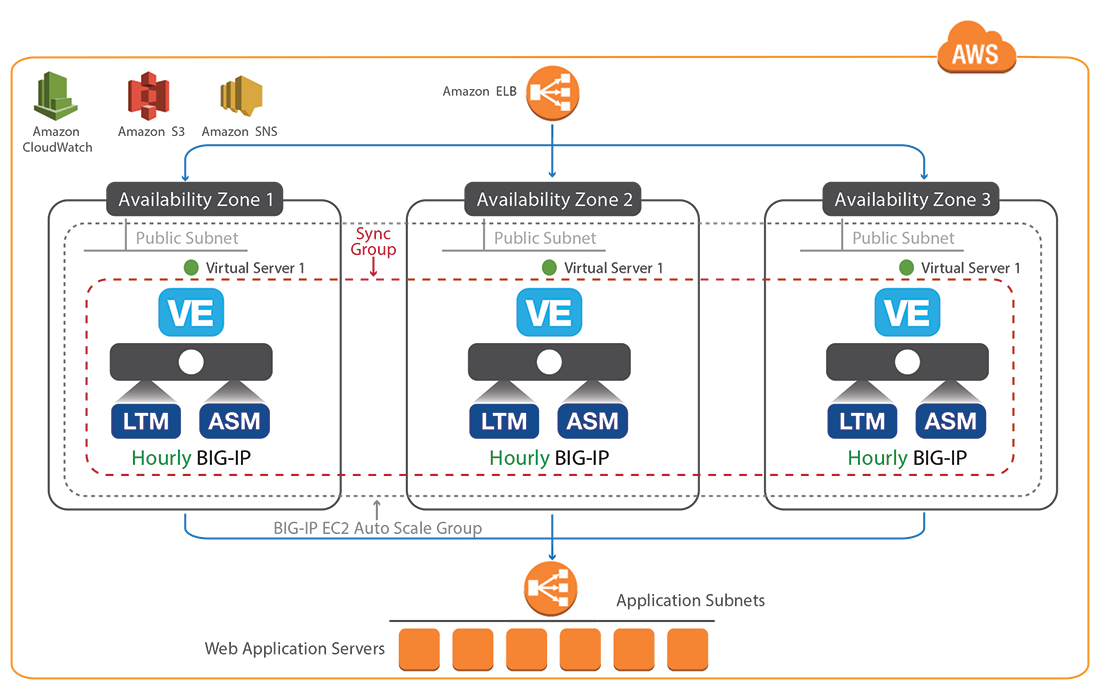
New Auto Scaling Standalone Waf Solution For Amazon Aws
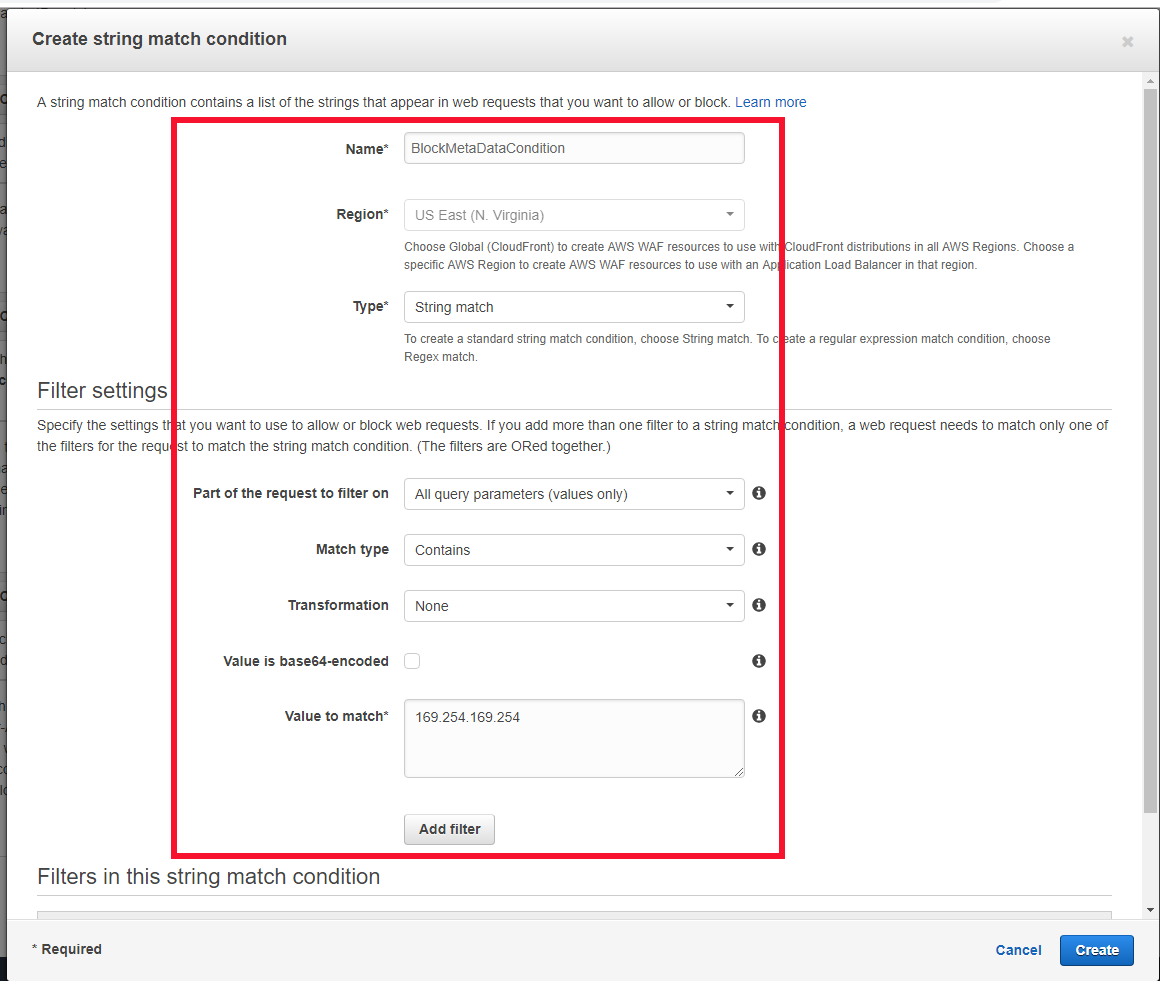
How To Secure Web Applications With Aws Waf Edureka

Amazon Web Services Aws Web Application Firewall Waf Service Delivery In Dubai Abu Dhabi And Uae

Tn Marketing Grows Cloud Security With Aws Waf Managed Rules Flux7

How To Use Amazon Guardduty And Aws Web Application Firewall To Automatically Block Suspicious Hosts Aws Security Blog

Aws Waf Vs Prestashop What Are The Differences

Using Aws Waf To Secure Wordpress Login Hydras
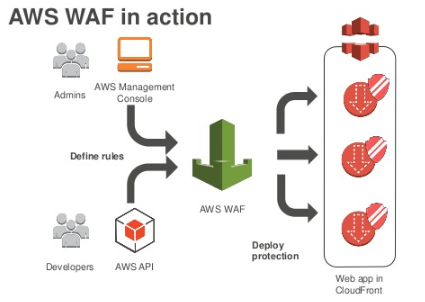
Aws Waf Web Application Firewall With Preconfigured Cloudformation Template And Web Acl For Cloudfront Distribution
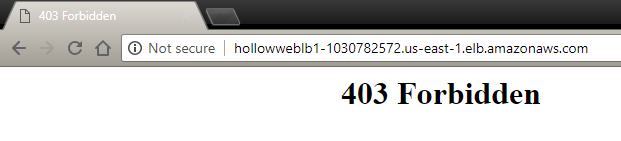
Add Aws Web Application Firewall To Protect Your Apps The It Hollow

Install The Aws Waf App And View The Dashboards Sumo Logic

Use Aws Waf To Block Malicious Requests Cloudaxis

Aws Waf Vs Modsecurity Kevinhakanson Com
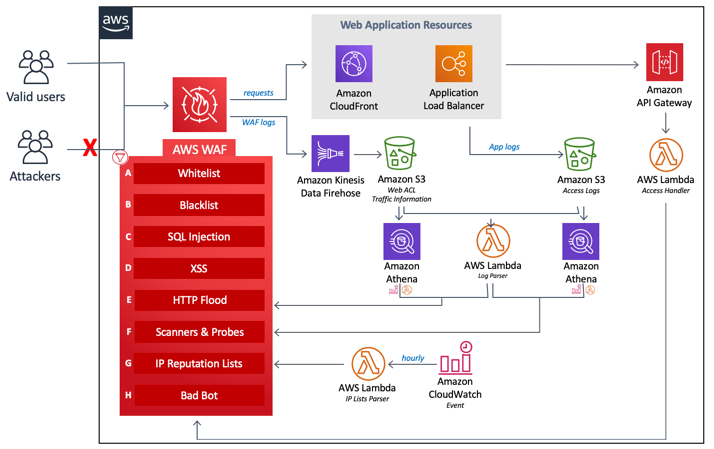
Jeff Barr Very Helpful Aws Waf Security Automations T Co Seqvt9edpl Automatically Deploy A Set Of Aws Waf Rules Designed To Filter Common Web Based

Security In Serverless Introduction By Kirill Kolyaskin Medium
1

Using Waf And Cloudfront With Serverless Applications Scalesec
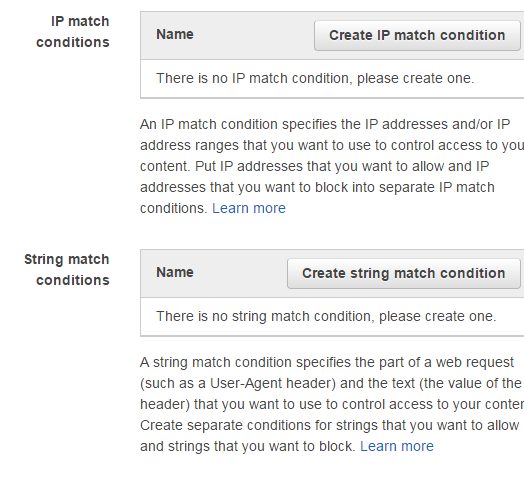
Aws Waf Web Application Firewall And Application Security

Origin Protection With Aws Waf Shield

Sun Coree Db
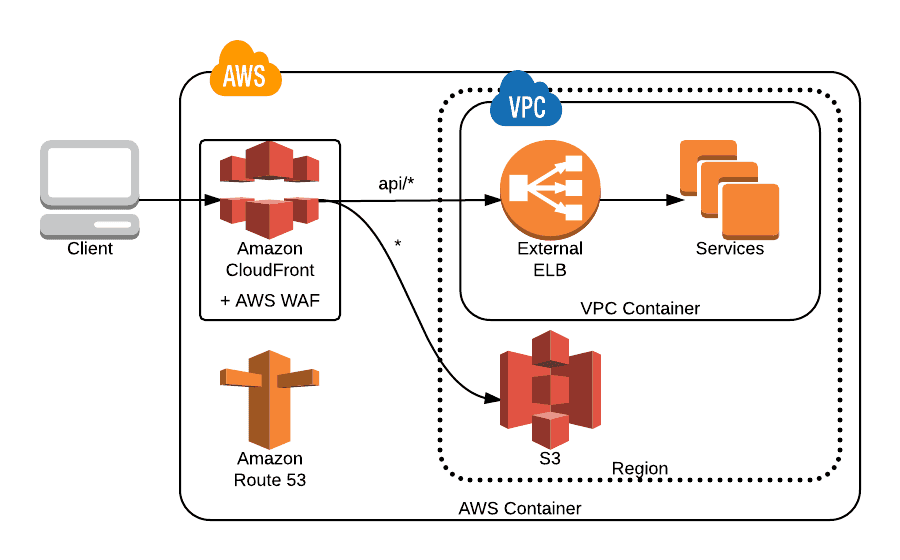
Aws Waf Vs Modsecurity Kevinhakanson Com

Aws Waf Web Application Firewall Aws Newbies

Github Traveloka Terraform Aws Waf Webacl Supporting Resources A Module To Create Several Resources Needed By Aws Waf Webacl

Aws Waf Aws Security Blog
1

Monitoring Aws Waf With New Relic

Fortinet Delivers Advanced Web Application Protection Through New Managed Rules For Aws Waf Service

Generating Amazon Web Services Waf Rules From Netsparker Standard Netsparker
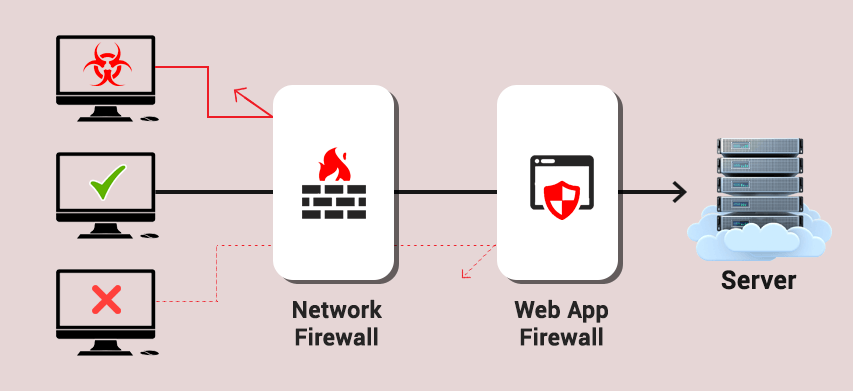
Aws Waf A Cost Effective Web Application Firewall For Your Saas Application Mobisoft Infotech
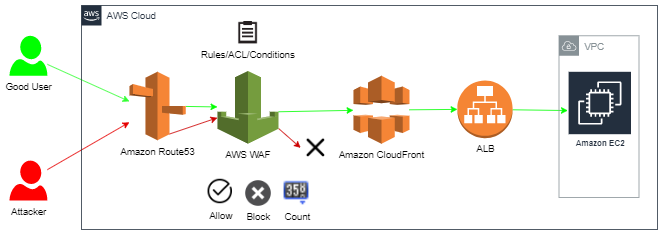
Aws Waf And Csrf Rule The What Why And How By Shouki Souri Medium
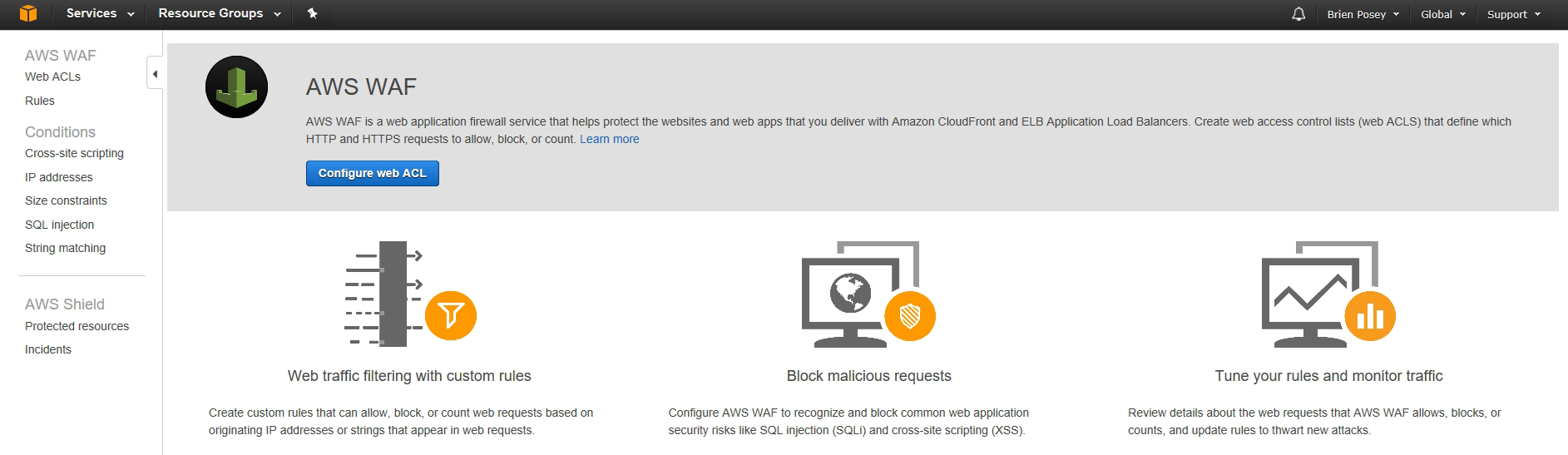
Deploying A Web Application Firewall On Aws Awsinsider
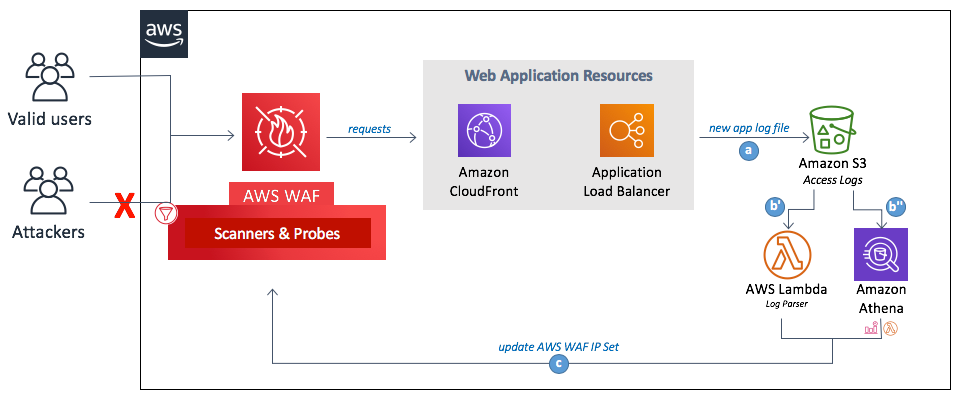
Aws Cloudformation 을 사용한 Waf 자동 구축 및 운영 Grip News

Automatically Updating Aws Waf Rule In Real Time Using Amazon Eventbridge Aws Security Blog

Aws Waf How It Helps Organizations To Secure Their Web Applications From Common Web Exploits Rapyder Cloud Solutions

Increase Security Posture And Troubleshoot Service Delivery With Splunk New Aws Waf Full Logs Feature Splunk
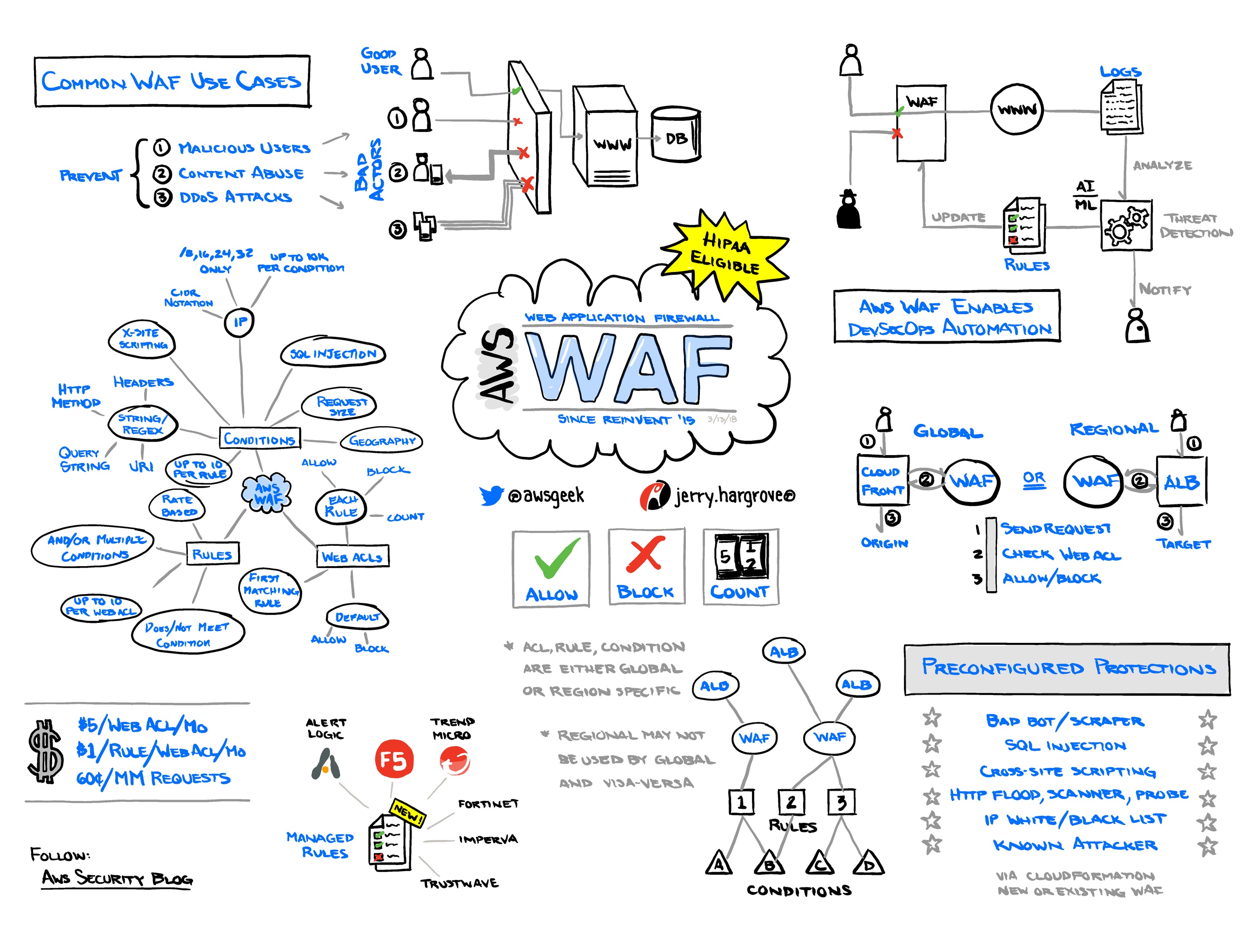
Jerry Hargrove Aws Waf

An Introduction Into Aws Waf Web Application Firewall Articles Resources And News For Business

How To Analyze Aws Waf Logs Using Amazon Elasticsearch Service Aws Security Blog




