Trendmicro Deepsecurity
Trend Micro Apex One is ranked 11th in Endpoint Protection (EPP) for Business with 25 reviews while Trend Micro Deep Security is ranked 1st in Virtualization Security with 11 reviews Trend Micro Apex One is rated 78, while Trend Micro Deep Security is rated The top reviewer of Trend Micro Apex One writes "Antivirus and Malware scanning.
Trendmicro deepsecurity. C Supported in Deep Security Virtual Application 1 Update 3, there is a couple of known issues when deploying Deep Security Virtual Appliance (DSVA) in NSXT 25 due to changes in NSXT 25, for more detail see KB;. Trend Micro Virtual Network Function Suite(TM VNFS) VNFS Director 143 is validated on Nutanix AHV (AOS ) Trend Micro Deep Security 96 is validated on ESXi, HyperV, and Nutanix AHV (AOS 414) TrendMicro Server Protect for Storage 60 is Integrated with Nutanix Files ( AOS 515). CylancePROTECT is rated , while Trend Micro Deep Security is rated The top reviewer of CylancePROTECT writes "An outstanding product that is pretty spot on and easy to deploy and use" On the other hand, the top reviewer of Trend Micro Deep Security writes "Each and every IP connecting to the server gets scanned so we can block.
Trend Micro Deep Security secures more servers globally than anyone else and has seamlessly integrated with AWS to ensure security won't impact cloud agility or autoscaling Pricing information The Deep Security AMI needs to run on an EC2 instance. Easily activate and register security products and services from the extensive Trend Micro product line Smarter Access all your Trend Micro security products and services from a central location online Simpler Logon once for access to all Trend Micro products and services on the portal. Purpose built for your deployments, Trend Micro Cloud One™ – Workload Security, powered by XGen™, delivers the operational efficiency required to support and secure your modern data center, including physical servers and software, virtual servers, and desktop.
Deep Security as a Service will soon make a transition to Trend Micro Cloud One Workload Security Please start signing in to Cloud One with your existing credentials here https//cloudonetrendmicrocom Learn more about the transition to Cloud One here. Software from the Trend Micro Download Center to the Deep Security Manager 3 When the software has finished downloading, a green check mark will appear in the Imported column for that Agent. Deep Security Manager connects to the Internet to download the software from Trend Micro Download Center The manager then checks the digital signature on the software package When the manager has finished, a green check mark appears in the IMPORTED column for that agent.
Trend Micro Deep Security DSM RPM;. Deep Security OnlineHelp for Allnoarch Trend Micro Deep SecurityDeep Security OnlineHelp for Allnoarch. Where the default is /opt/dsm (Linux) or C\Program Files\Trend Micro\Deep Security Manager (Windows) Within the above directory, two types of files are created TPlantxt This file contains all data definition language (DDL) SQL statements that the installer will use to update the schema.
For details about which specific releases are supported, see Deep Security Support for Windows 10 and Deep Security Support for Windows Server Core (3) All Trend Micro testing on Windows Embedded platforms is performed in a virtualized environment Because these operating systems are typically run on custom hardware (for example, on pointof. Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice Before Trend Micro, the Trend Micro tball logo, Deep Security, Control Server Plugin, Damage Cleanup Services, eServer Plugin, InterScan,. To do a silent installation of Deep Security Agent Create a temp folder under C\ Copy and extract the Deep Security Agent MSI installer into c\temp Make sure you have noted the correct folder location and MSI package name, pay attention to extension names.
Deep Security as a Service is now Trend Micro Cloud One Workload Security Deep Security as a Service release notes have moved to What's New in Workload Security Deep Security as a Service is now Trend Micro Cloud One Workload Security Please go to the Workload Security help for the latest content and update your bookmarks accordingly. Deep Security URLs If you need to restrict the URLs that are allowed in your environment, read this section You'll need to make sure your firewall allows traffic to the following Trend Micro, Deep Security, AWS, and Azure server URLs on port 443 (HTTPS) and port 80 (HTTP). Deep Security feature releases Major releases of Deep Security Manager, such as Deep Security Manager 100, are made available on an annual basis, and include new functionality and enhancements for existing functionality Feature releases are interim versions of Deep Security that provide early access to new functionality and are made available at regular intervals between major releases.
C\Program Files\Trend Micro\Deep Security Agent>dsa_control selfprotect 0 Go to the Control Panel and select Uninstall a program Look for the Trend Micro Deep Security Agent and then select Uninstall Alternatively, you can uninstall from the command line msiexec /x For a silent uninstall, add /quiet. C Supported in Deep Security Virtual Application 1 Update 3, there is a couple of known issues when deploying Deep Security Virtual Appliance (DSVA) in NSXT 25 due to changes in NSXT 25, for more detail see KB;. Deep Security and VMware compatibility matrix;.
Deep Security powers Trend Micro?s Cloud and Data Center Security solution, providing marketleading security capabilities for physical, virtual, and cloud servers from a single integrated platform Enhances the security and visibility of workloads across private, public and hybrid clouds in a softwaredefined datacenter. Trend Micro Deep Security 96 As the demand for cloud and data center security grows, we are happy to introduce Deep Security 96 This marketleading solution delivers the most advanced cloud and data center security platform, seamlessly protecting customer deployments across their physical, virtual and cloud environments About Deep Security 96. Create a free account on Trend Micro Cloud One to try out Cloud One Workload Security (formerly Deep Security as a Service).
Learn what your peers think about Trend Micro Deep Security Get advice and tips from experienced pros sharing their opinions Updated November Download now 452,265 professionals have used our research since 12 Rayees Tamton Data Center Manager/Support Delivery Manager at Salam Technology. D Supports Agentless Endpoint Protection (Guest Introspection) in Deep Security Manager (12 FR 429). Download software for Deep Security long term support releases.
Deep Security as a Service will soon make a transition to Trend Micro Cloud One Workload Security Please start signing in to Cloud One with your existing credentials here https//cloudonetrendmicrocom Learn more about the transition to Cloud One here. Deep Security XDR offer eligible to customers utilizing the software version Customers with Trend Micro Cloud One™ – Workload Security (previously known as Trend Micro™ Deep Security™ as a Service) are not eligible Email XDR offer eligible to customers without XDR Addon Cloud App Security license. Trend Micro Research has developed a goto resource for all things related to cybercriminal underground hosting and infrastructure Today we released the second in this threepart series of reports which detail the what, how, and why of cybercriminal hosting (see the first part here) As part of this report, we dive into the common life.
Deep Security Manager connects to the Internet to download the software from Trend Micro Download Center The manager then checks the digital signature on the software package When the manager has finished, a green check mark appears in the IMPORTED column for that agent. Trend Micro virtual patching solutions deliver immediate protection while eliminating the operational pains of emergency patching, frequent patch cycles, and costly system downtime Deep Security virtual patching keeps your servers and endpoints protected while reducing the risk of breach disclosure costs. Check out alternatives and read real reviews from real users.
Get proactive protection for your Azure workloads and containers with Trend Micro™ Deep Security™ Built to work seamlessly with Azure, Deep Security provides a complete suite of runtime security capabilities for your virtual machines and container environments Prevent network attacks with Intrusion detection and prevention (IDS/IPS). Trend Micro™ WiFi Protection Turn public hotspots into secure WiFi connections with a Virtual Private Network (VPN) using bankgrade data encryption to keep your information safe from hackers Starting at $2995/yr for 1 device Learn more. Trend Micro Education Team Trend Micro™ Deep Security Training for Certified Professionals Course Description In this course, you will learn how to use Trend Micro™ Deep Security This course provides information about the basic architecture, deployment scenarios,.
Trend Micro™ Deep Security™ protège automatiquement les charges de travail nouvelles et existantes, même face aux menaces inconnues, grâce à des techniques spécifiques de type apprentissage automatique ou patch virtuels Un panel complet de fonctions de sécurité proposé par un seul agent intelligent. Sign into your Trend Micro account to manage your consumer software subscriptions. Trend Micro Virtual Network Function Suite(TM VNFS) VNFS Director 143 is validated on Nutanix AHV (AOS ) Trend Micro Deep Security 96 is validated on ESXi, HyperV, and Nutanix AHV (AOS 414) TrendMicro Server Protect for Storage 60 is Integrated with Nutanix Files ( AOS 515).
Deep Security as a Service is now Trend Micro Cloud One Workload Security The help for that product is available at. Trend Micro Global Technical Support Guide for Business Customers;. Get proactive protection for your Azure workloads and containers with Trend Micro™ Deep Security™ Built to work seamlessly with Azure, Deep Security provides a complete suite of runtime security capabilities for your virtual machines and container environments Prevent network attacks with Intrusion detection and prevention (IDS/IPS).
Get proactive protection for EC2 workloads with Trend Micro Deep Security Secure hybrid environments with the Deep Security AMI and pay hourly per workload protected Buy and deploy a Deep Security AMI and protect your physical, virtual or cloud resources with an agent or our industry leading virtual appliance, and pay for it all on your AWS bill. Deep Security as a Service is now Trend Micro Cloud One Workload Security Please go to the Workload Security help for the latest content and update your bookmarks accordingly You'll be redirected automatically in seconds. Windows Server 08 and 08 R2 reached End of Support on 14 th January , raising security issues for any systems running these platforms With Trend Micro Deep Security and Trend Micro Cloud One™ there’s no need to be concerned.
Trend Micro Deep Security for Splunk Overview This package contains parsing logic, saved searches, and dashboards for monitoring Trend Micro Deep Security through Splunk. Get up and running in minutes!. Let your peers help you Read real Trend Micro Deep Security reviews from real customers At IT Central Station you'll find reviews, ratings, comparisons of pricing, performance, features, stability and more Don't buy the wrong product for your company Let us help.
Configure your Trend Micro Deep Security device to send syslog events to QRadar If QRadar does not automatically detect the log source, add a Trend Micro Deep Security DSM log source on the QRadar Console The following table describes the parameters that require specific values for Trend Micro. Trend Micro is the global leader in enterprise data security and cybersecurity solutions for businesses, data centers, cloud environments, networks, and endpoints. Deep Security XDR offer eligible to customers utilizing the software version Customers with Trend Micro Cloud One™ – Workload Security (previously known as Trend Micro™ Deep Security™ as a Service) are not eligible Email XDR offer eligible to customers without XDR Addon Cloud App Security license.
Don't have an account?. This article enumerates all the log files available in Deep Security Know the location, description, and maximum size for each log file. Python SDK The Deep Security Python SDK consists of a package containing the module that you can use to interact with the API If you would rather use the API directly via tools such as Postman and curl, you do not need an SDK.
Trend Micro Deep Security for Splunk Overview This package contains parsing logic, saved searches, and dashboards for monitoring Trend Micro Deep Security through Splunk. Download the Deep Security SDK for developers and learn how to automate host security at the speed of DevOps with the new REST API. Manually uninstalling Deep Security Agent, Relay, and Notifier from Windows "Communications Problem Detected" appears on a machine managed by the Deep Security Manager (DSM).
Deep Security as a Service is now Trend Micro Cloud One Workload Security Please go to the Workload Security help for the latest content and update your bookmarks accordingly You'll be redirected automatically in seconds Looking for Deep Security help?. Trend Micro Deep Security is a server protection solution which gives you a great variety of modules from which we can protect the servers from most advance and recent threatsIt is the only solution with having the capability for vulnerability patching mechanism which is the USP of the product. Deep Security powers Trend Micro?s Cloud and Data Center Security solution, providing marketleading security capabilities for physical, virtual, and cloud servers from a single integrated platform Enhances the security and visibility of workloads across private, public and hybrid clouds in a softwaredefined datacenter.
Deep Security as a Service is now Trend Micro Cloud One Workload Security Please go to the Workload Security help for the latest content and update your bookmarks accordingly You'll be redirected automatically in seconds Looking for Deep Security help?. With the help of Capterra, learn about Trend Micro Deep Security, its features, pricing information, popular comparisons to other Cloud Security products and more Still not sure about Trend Micro Deep Security?. Trend Micro's Deep Security is an intelligent data protection solution that services all environments and was built purposefully to support VMware deployments.
This Quick Start automatically deploys Trend Micro Deep Security on AWS, using AWS services and best practices Trend Micro Deep Security is a hostbased security product that provides Intrusion Detection and Prevention, AntiMalware, Host Firewall, File and System Integrity Monitoring, Log Inspection, and Content Filtering modules in a single agent running in the guest operating system. Deep Security OnlineHelp for Allnoarch Trend Micro Deep SecurityDeep Security OnlineHelp for Allnoarch. Trend Micro Deep Security as a Service.
Trend Micro Deep Security secures more servers globally than anyone else and has seamlessly integrated with AWS to ensure security won't impact cloud agility or autoscaling Pricing information The Deep Security AMI needs to run on an EC2 instance. D Supports Agentless Endpoint Protection (Guest Introspection) in Deep Security Manager (12 FR 429). Trend Micro virtual patching solutions deliver immediate protection while eliminating the operational pains of emergency patching, frequent patch cycles, and costly system downtime Deep Security virtual patching keeps your servers and endpoints protected while reducing the risk of breach disclosure costs.
Software from the Trend Micro Download Center to the Deep Security Manager 3 When the software has finished downloading, a green check mark will appear in the Imported column for that Agent. Trend Micro™ Deep Security™ can automatically protect new and existing workloads against even unknown threats with techniques like machine learning and virtual patching A full range of security capabilities in a single smart agent Protection against vulnerabilities and for endoflife systems.

Deep Security Archives Pagina 2 Van 2 Blog Trendmicro Nl
Q Tbn And9gcspgocitmfqevpqdf7rbdjow3rng3nzbzldpyxa Nczwkxzjqqc Usqp Cau

Installing And Configuring Trend Micro Deep Security Vsphere And Nsx Environment On Aws And Google Cloud Ravello Blog
Trendmicro Deepsecurity のギャラリー

Deepsecurity

Aws Security Hub And Deep Security

Trend Micro Wikipedia

Trend Micro Compuset
Common Issues In Deep Security 10 0
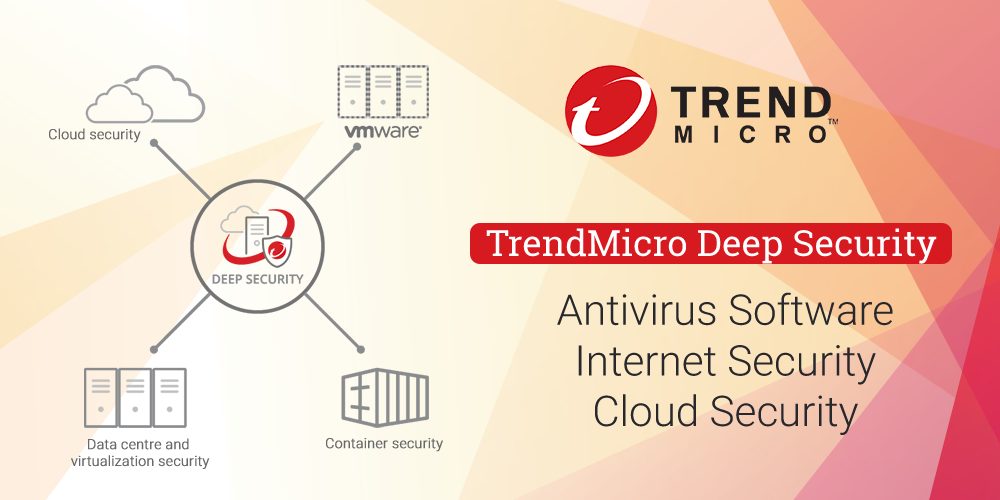
Trend Micro Deep Security And Its Enforce Security Controls

Deepsecurity
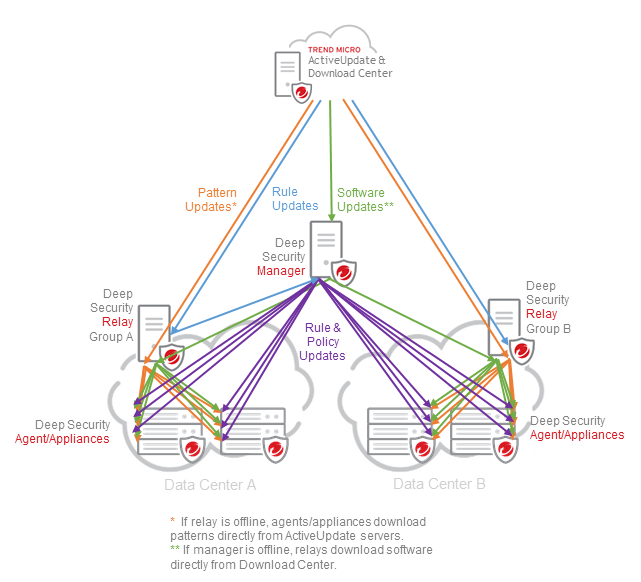
Deploy Deep Security Deep Security

Trend Micro Deep Security Reviews 21 Details Pricing Features G2
Q Tbn And9gctibvw7nyly7h9jep9wmznn6dkc Dz Euyqcjiphsenfvjnvqdl Usqp Cau

Trend Micro Deep Security For 1 Year Visaag Technologies Private Limited Id

Trend Micro Diepe Beveiliging Op Een Virtuele Machine Installeren Azure Virtual Machines Microsoft Docs

Trend Micro Deep Security 7 5 Sp1 User S Guide

Virtualization Security Server Virtualization Deep Security Trend Micro

Trend Micro Deep Security And Nsx 6 2 3 Issue Vmbaggum

Deep Security On Aws Quick Start

Extend Protection To Vmware Cloud On Aws With Trend Micro Deep Security

Trend Micro Deep Security Siem Log Event Correlation Trend Micro Deep Security Log Alerting Netsurion

Trend Micro Deep Security Malware Prevention Trenddefense Com

Trend Micro Deep Security Help

Trend Micro Deep Security 8 Available Now
Checking If The Modules Are Functioning Deep Security

Trendmicro Deepsecurity Fortisoar 1 1 0 Fortinet Documentation Library

How Does Trend Micro Deep Security Work Clean My Pc
Trend Micro Deep Security Smart Check Trend Micro

Deep Security 12 Agentless To Agent Based Migration Youtube

Holistic View Of The Deep Security Solution Trend Micro

Iot Cloud Cloudsolutionsiot Com Que Es Deep Security De Trendmicro
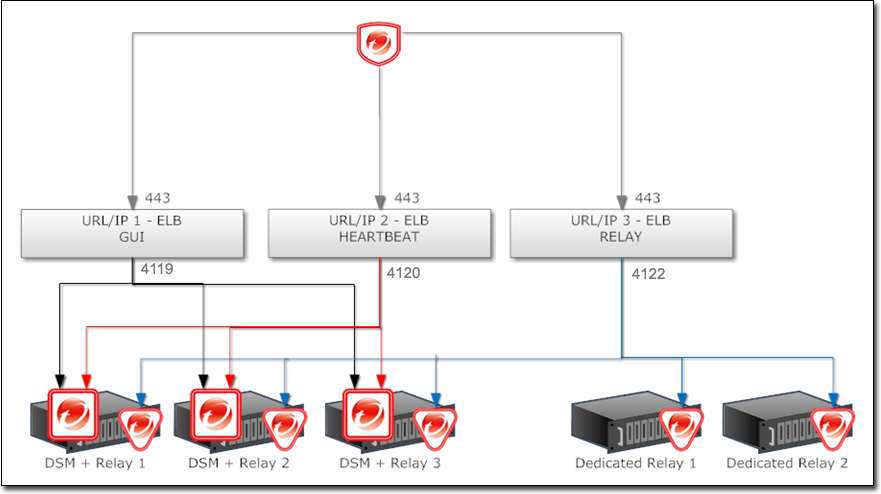
Deploy Additional Relays Deep Security

Deep Security Software Runtime Security For Workloads Trend Micro

Trend Micro Ct Link Systems Inc

Trend Micro Deep Security Siem Log Event Correlation Trend Micro Deep Security Log Alerting Netsurion

Introduction Trend Micro Deep Security

Trendmicro Deepsecurity Fortisoar 1 1 0 Fortinet Documentation Library

Deepsecurity

Trend Micro Deep Security Packages Insight

Trend Micro Deep Security
Checking If The Modules Are Functioning Deep Security

Extending Trend Micro S Container Protection With Deep Security Smart Check

Introduction Trend Micro Deep Security

Trendmicro Deep Security Monitoring With Vrealize Operations Virtualization Blog

How To Video Trend Micro Deep Security On Aws
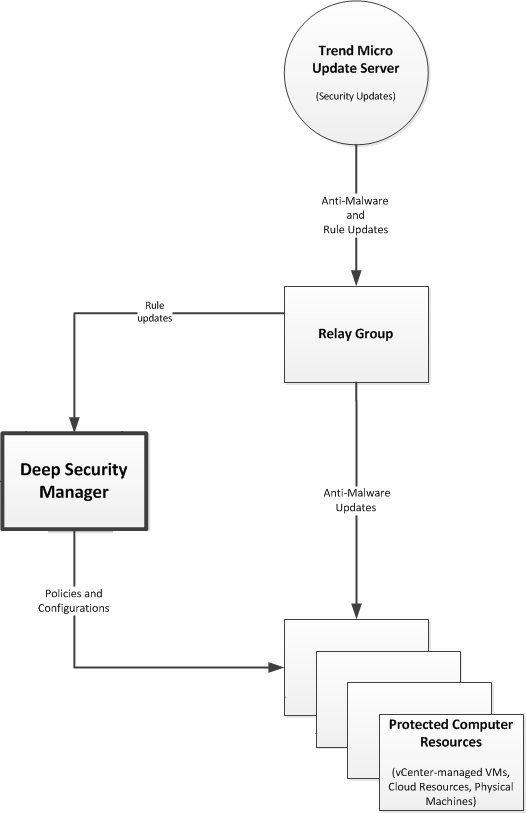
Ensure Your Computers Have The Latest Threat Information Deep Security

How To Configure Trendmicro Deepsecurity For Aws Using Cloudformation Binx

Trend Micro Deep Security Help
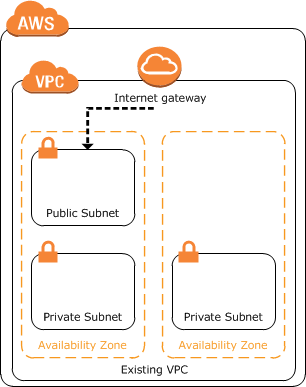
Step 1 Set Up A Vpc Trend Micro Deep Security On Aws
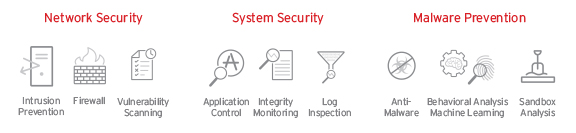
Data Center Security Trend Micro Deep Security
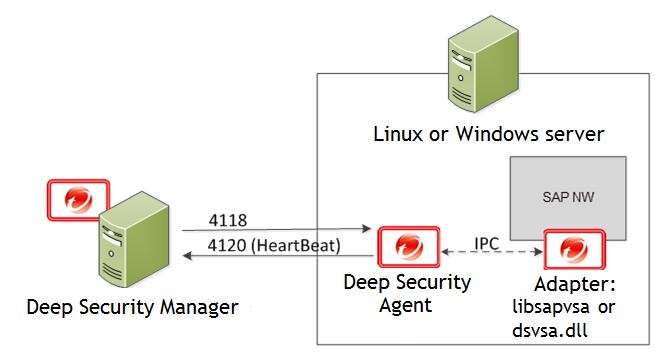
Set Up Sap Integration Deep Security

Step 4 Log In To The Deep Security Manager Console Trend Micro Deep Security On Aws

Trend Micro Deep Security

Trend Micro Extends Container Security Solution With Deep Security Smart Check

Trend Micro Deep Security
Install Deep Security Agent On Linux Deep Security

Trend Micro Deep Security Vmware Vshield Endpoint
Deep Security For Vmware Youtube
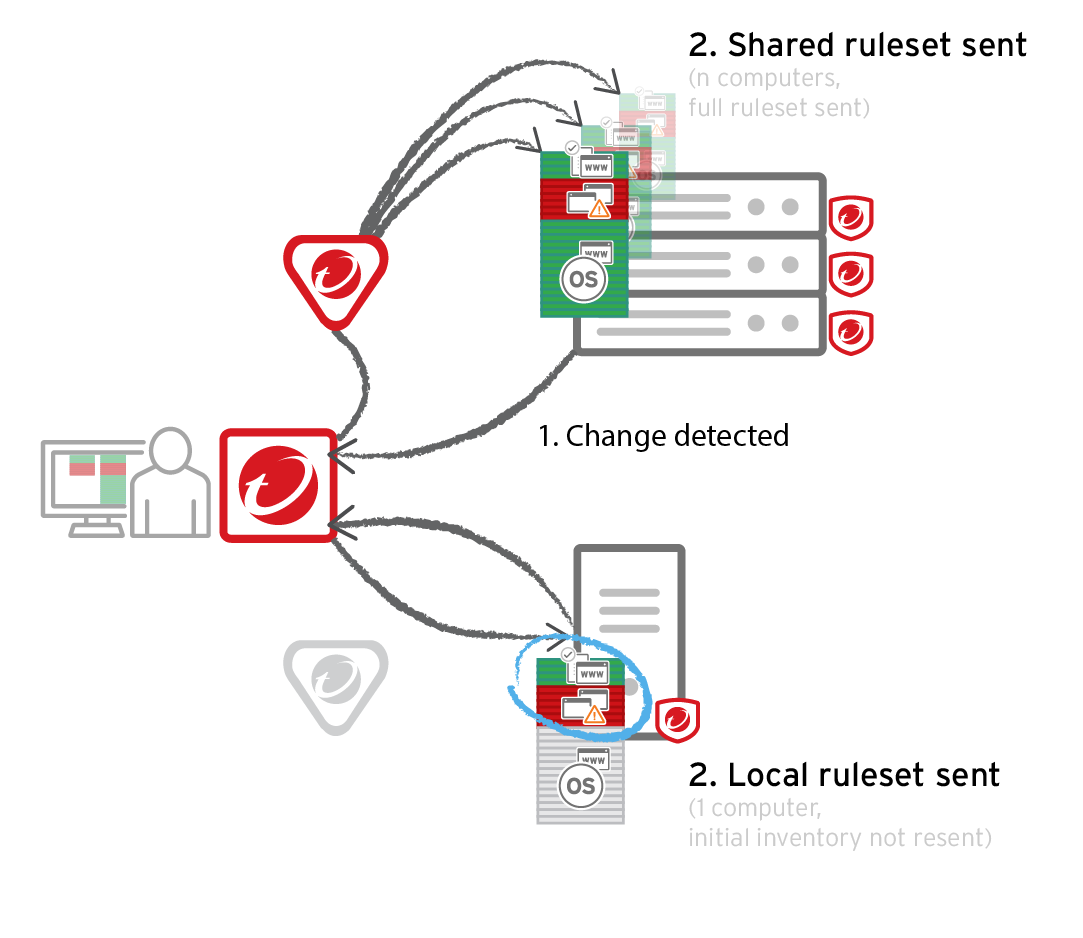
Lock Down Software With Application Control Deep Security

Trend Micro Deep Security For The Data Center

Trendmicro Deepsecurity Case Testimonal

Trend Micro Dsm Doesn T Update Anymore Ddezoete Nl

Trend Micro Tech Tv Deep Security Agentless Anti Malware Youtube

Trend Micro Deep Security Manager Azure Cloud Deployment Antivirusonline

Trend Micro Deep Security Getting Started And Installation Guide

Aws Marketplace Trend Micro Deep Security

Deep Security Integration With Operations Management Suite Oms Trend Micro
Trend Micro Deep Security Relay Agent Install Bytesizedalex
Q Tbn And9gcspgocitmfqevpqdf7rbdjow3rng3nzbzldpyxa Nczwkxzjqqc Usqp Cau

Trendmicro Specialists Trendmicro Ndm

Trend Micro Diepe Beveiliging Op Een Virtuele Machine Installeren Azure Virtual Machines Microsoft Docs

How To Install Trend Micro Deep Security Using Sql Express Trend Micro How To Uninstall Micro
Things I Ve Found Helpful Trend Micro Deep Security Visio Stencil

Trend Micro Deep Security 11 0 Installation Step By Step 18 Archives Techtabinfo
Anti Malware Engine Offline Errors And Solutions Deep Security
Http Www2 Techdata Nl 18 Pdf Deepsecurity11 Pdf
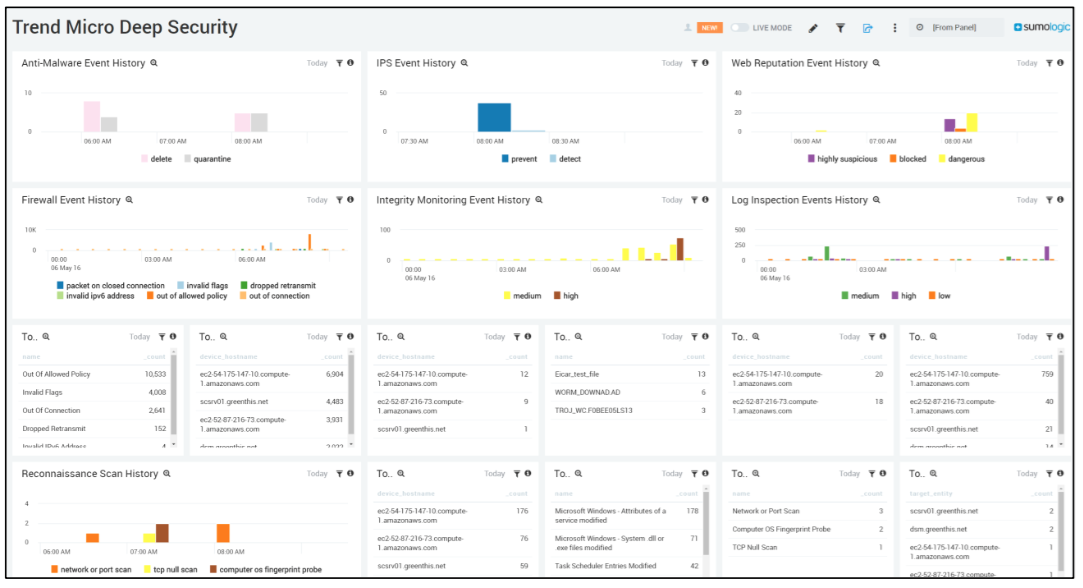
Improving Your Security Posture With Trend Micro Deep Security Integration Sumo Logic
Cdw Prod Adobecqms Net Content Dam Cdw On Domain Cdw Brands Trend Mirco Ds01 Deep Security Software Web Pdf

クラウドサーバセキュリティ Trend Micro Deep Security アズジェント

Trend Micro Deep Security Reference Architecture

Trend Micro Deep Security Platform For Virtualized Environments

How Does Trend Micro Deep Security Work Clean My Pc
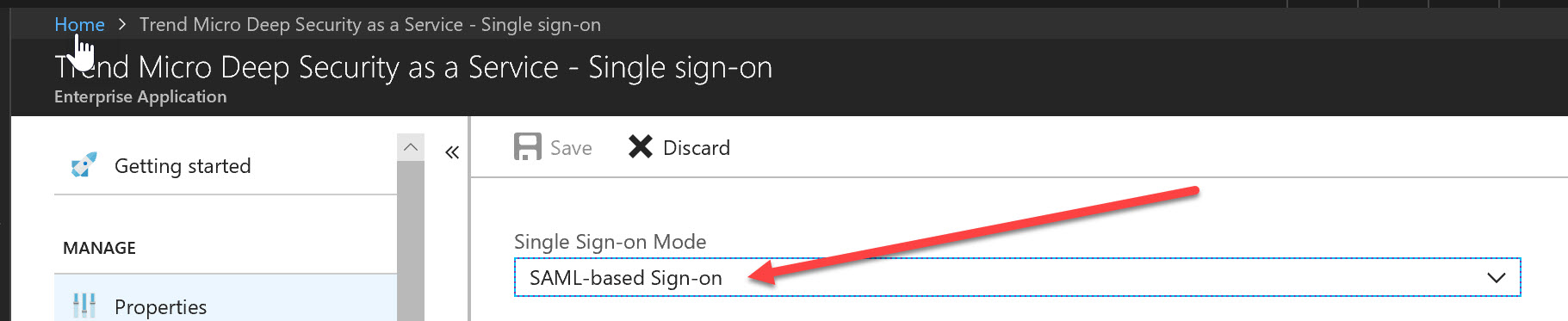
Trend Micro Deep Security Saml Integration With Azure Active Directory Cloud Azzurri

Trend Micro Deep Security For Splunk Splunkbase

Product Sheet How Trend Micro Deep Security Keeps You Safe Trend Micro

Trend Micro Deep Security 9 5 Deep Security Virtual Appliance Dsva Part 5 Techbrainblog

Vmware Environments Archives Trend Micro
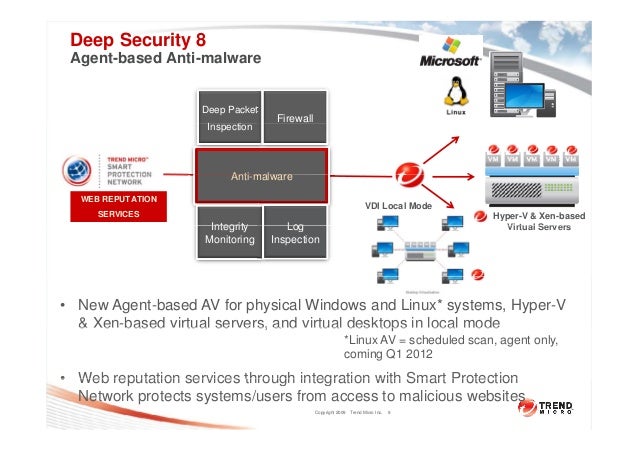
Introduction Trend Micro Deep Security
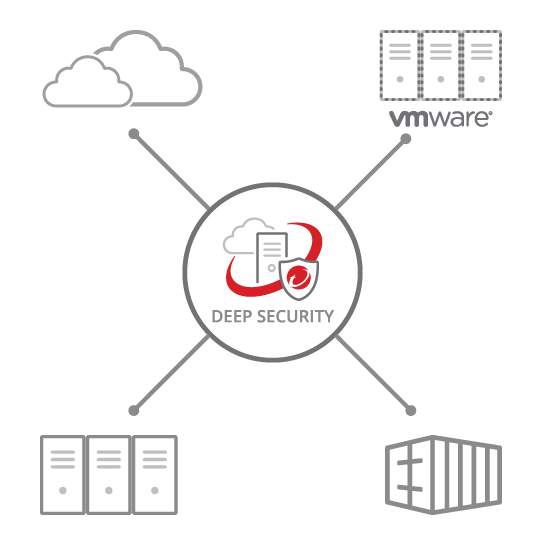
Data Center And Virtualization Security Trend Micro Deep Security

Trend Micro Deep Security Techbrainblog

Trend Micro Deep Security Ssl Traffic Inspection
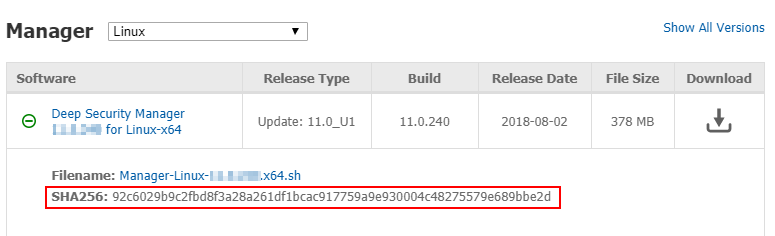
Deploy Deep Security Deep Security

Trend Micro Deep Security For Splunk Splunkbase
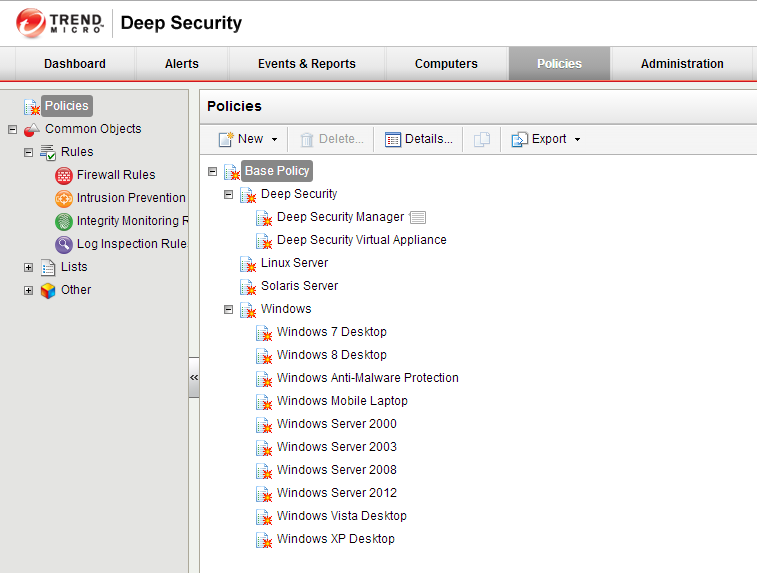
Vshield Endpoint Trend Micro Deep Security Part 3 The It Hollow
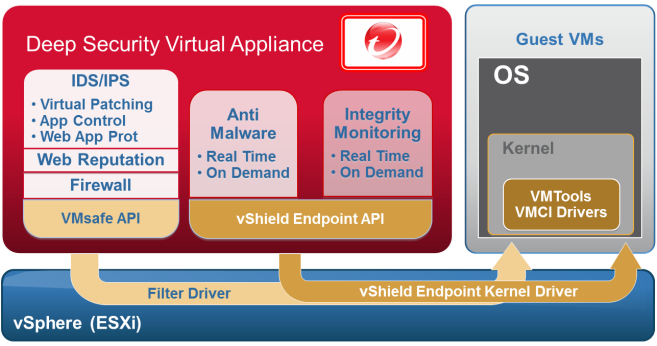
Trend Micro Deep Security

Trend Micro Certified Professional Deep Security Dartalis The Art Of Information Security
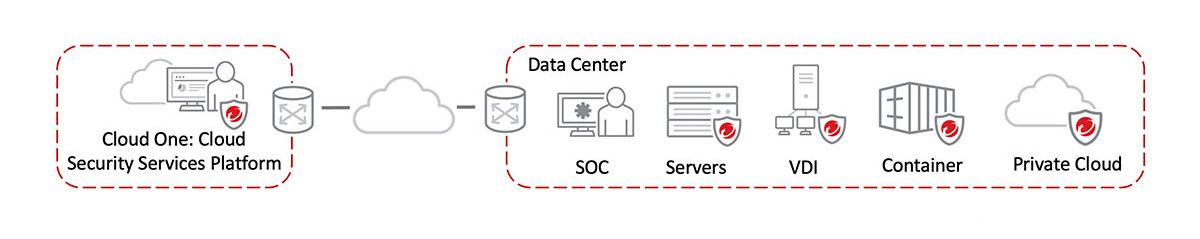
Data Center Security Trend Micro Deep Security

Trend Micro Deep Security
Trend Micro Middle East And Africa Get Trendmicro Deepsecurity And Protect Your Physical Virtual And Cloud Servers It S Guaranteed To Stop Network Attacks Lock Down Systems And Prevent Malware

Collect On Premises Logs For The Trend Micro Deep Security App Sumo Logic

Features Trendmicro Ndm

Trend Micro Deep Security 9 5 Sp1 Communications Security Establishment

Trendmicro Deep Security Monitoring With Vrealize Operations Virtualization Blog




