Aws Cloudhsm
Amazon Hardware Security Module (HSM) is a cloud service that uses dedicated HSM appliances within the AWS Cloud to help you design and deploy stringent data security solutions which meet regulatory and compliance requirements.

Aws cloudhsm. AWS CloudHSM comes with an hourly fee that changes based on your region of choice;. AWS CloudHSM is the name of Amazon’s original encryption key solution HSM stands for Hardware Security Module and in the solution provided by AWS, it is a Safenet Luna appliance hosted at AWS The appliance is single tenant and exclusive to each customer AWS only manages the hardware and base operation but does not manage the keys or even. Overview Cryptsoft CloudHSM® delivers full provider and consumer side capabilities using PKCS#11 v30 conformant interfaces for ease of integration into any environment where the security of an HSM solution is required.
CloudhsmCreateHsm Creates an uninitialized HSM instance. CloudHSM is delivered via singletenant access to a dedicated highly available cluster With KMS, you have the option of creating your own encryption keys or letting AWS do that for you CloudHSM works only with keys that you create This gives you greater control as AWS has no access to the keys that you generate. Amazon Web Services' CloudHSM is not your mother's cloud security tool And that's a good thing if you need the highest possible level of security and compliance in the cloud CloudHSM is the first Amazon service to offer companies complete control of their most sensitive cloud data while in the public cloud.
AWS CloudHSM provides hardware security modules in the AWS Cloud A hardware security module (HSM) is a computing device that processes cryptographic operations and provides secure storage for cryptographic keys When you use an HSM from AWS CloudHSM, you can perform a variety of cryptographic tasks. Complete AWS IAM Reference;. AWS CloudHSM Show transcript Advance your knowledge in tech Get all the quality content you’ll ever need to stay ahead with a Packt subscription access over 7,500 online books and videos on everything in tech Start Learning for FREE In this video, we will learn about CloudHSM, use cases and capabilities.
The AWS CloudHSM is the newer offering from AWS based on Cavium, not to be confused with the SafeNetbased AWS CloudHSM Classic For more information, refer to the AWS CloudHSM User Guide The EJBCA Cloud and AWS CloudHSM integration includes the following and more steps. CloudHSM offers exciting potential, so I wanted to share the important details, along with six caveats to consider as you think about CloudHSM Simply put, AWS CloudHSM is a service that can securely generate, store, and manage cryptographic keys Until now there was no really good way to use and manage cryptographic keys in the public cloud. Learning Objectives Educate customers in the types of problems CloudHSM solves for them Build customer trust in the ability of CloudHSM to secure their w.
AWS CloudHSM is a fully managed service that takes care of administrative, timeconsuming tasks such as backups, software updates, hardware provisioning, and high availability by automating these tasks However, AWS does not have any access to configure, create, manage, or use your CloudHSM. Cryptsoft CloudHSM® encapsulates Cryptsoft's experience in the key management and security market space and can be deployed into almost any environment with the ability to enhance, integrate with, or replace existing standards based or proprietary solutions. AWS CloudHSM 's Features Protect and store your cryptographic keys with industry standard, tamperresistant HSM appliances No one but you has access to your keys (including Amazon administrators who manage and maintain the appliance).
AWS Cloud HSM is a cloudbased HSM service in the Amazon Web Services The CloudHSM uses FIPS 1402 Level 3 certified Cavium/Marvell HSMs in the backend and is accessible using the PKCS#11 API Custom modules are needed for full EJBCA support of the CloudHSM, and this is supported in the EJBCA Cloud. Action Description Resources Conditions ;. Complete AWS IAM Reference;.
This is the official Amazon Web Services (AWS) documentation for AWS CloudHSM, a web service that provides cost effective hardware key management at cloud scale for sensitive and regulated workloads AWS CloudHSM provides a managed hardware security module (HSM) that enables you to easily generate and use your own encryption keys on the AWS Cloud. AWS CloudHSM is a cloudbased hardware security module that is customerowned and managed AWS CloudHSM acts as a singletenant on hardware restricting it from being shared with other customers and applications. CloudhsmCreateLunaClient Creates an HSM client * Global Conditions;.
For information about the current version of AWS CloudHSM, see AWS CloudHSM, the AWS CloudHSM User Guide, and the AWS CloudHSM API Reference Modifies the certificate used by the client This action can potentially start a workflow to install the new certificate on the client's HSMs. Action Description Resources Conditions ;. What is CloudHSM CloudHSM is one of the many services from Amazon ( AWS ) If you are familar with HSM it is a HSM sitting in the Amazon Data center CloudHSM's are not Virtualized and these are Physical devices sitting in Amazon Data centers(VPC) CloudHSM's are SafeNet Luna provisioned in the AWS VPC What is a HSM ( Hardware Security Module ).
Why Customers Choose CloudHSM • Reasons include – Control • Complete control of encryption keys, AWS cannot access key material • Finegrained control of how AWS assets can use your keys – Compliance • FIPS 1402 level 2 or 3 certification • Common Criteria EAL4 certification – Performance/Availability • When required, “local” CloudHSM much better than onprem – Network transit times – Usage patterns. AWS OpsWorks User Guide (13) by Amazon Web Services AWS CloudHSM User Guide (13) by Amazon Web Services AWS Elastic Beanstalk Developer Guide (13) by Amazon Web Services Amazon Web Services For Dummies (13) by Bernard Golden Getting Started with AWS (12) by Amazon Web Services AWS Identity and Access Management (IAM) User Guide. AWS KMS is a managed service that uses hardware security modules (HSMs) to protect the security of your encryption keys.
CloudHSM is one of the many services from Amazon (AWS) If you are familar with HSM it is a HSM sitting in the Amazon Data center CloudHSM's are not Virtualized and these are Physical devices sitting in Amazon Data centers(VPC) CloudHSM's are SafeNet Luna provisioned in the AWS VPC. CloudHSM offers exciting potential, so I wanted to share the important details, along with six caveats to consider as you think about CloudHSM Simply put, AWS CloudHSM is a service that can securely generate, store, and manage cryptographic keys Until now there was no really good way to use and manage cryptographic keys in the public cloud. For information about the current version of AWS CloudHSM, see AWS CloudHSM, the AWS CloudHSM User Guide, and the AWS CloudHSM API Reference Adds or overwrites one or more tags for the specified AWS CloudHSM resource Each tag consists of a key and a value keys must be unique to each resource.
AWS CloudHSM 's Features Protect and store your cryptographic keys with industry standard, tamperresistant HSM appliances No one but you has access to your keys (including Amazon administrators who manage and maintain the appliance). One of the services offered by Amazon Web Services (AWS) is AWS CloudHSM Classic CloudHSM is a hardware security module (HSM) that allows you to securely store keys and perform cryptographic operations on the device. CloudhsmCreateHsm Creates an uninitialized HSM instance.
CloudhsmCreateHapg Creates a highavailability partition group * Global Conditions;. AWS – CloudHSM CloudHSM (Hardware Security Module) This is essentially the name of a dedicated physical machine that is seperate from all the other AWS hardware, and it is used to store encryption keys If an outside party gains access to these keys, then your AWS infrastructure is compromised. AWS CloudHSM is a cryptographic service for making and keeping up equipment security modules (HSMs) in your AWS condition HSMs are computing devices that procedure cryptographic activities and give the secure capacity to cryptographic keys.
CloudhsmCreateHsm Creates an uninitialized HSM instance. The AWS CloudHSM service helps you meet corporate, contractual and regulatory compliance requirements for data security by using dedicated Hardware Security Module (HSM) appliances within the AWS cloud. AWS CloudHSM is a cloudbased hardware security module (HSM) that enables you to easily generate and use your own encryption keys on the AWS Cloud With CloudHSM, you can manage your own encryption keys using FIPS 1402 Level 3 validated HSMs.
Complete AWS IAM Reference;. Or the only possibility is to have an EC2 instance have some python boto scripts to be run to decrypt the file and then do a "COPY INTO" to snowflake Thanks,. The AWS CloudHSM service allows you to protect your encryption keys within HSMs designed and validated to government standards for secure key management You can securely generate, store, and manage the cryptographic keys used for data encryption such that they are accessible only by you.
CloudhsmCreateHsm Creates an uninitialized HSM instance. CloudhsmCreateHapg Creates a highavailability partition group * Global Conditions;. The AWS CloudHSM Service Level Agreement requires that you follow these guidelines Administration We recommend you create at least two cryptographic officers (COs) to administer your cluster Before setting quorum (MofN) policy, you must create at least M1 CO accounts Delete CO accounts with caution.
AWS CloudHSM helps meet corporate, contractual and regulatory compliance requirements for data security by using dedicated HSM appliances within the AWS cloud A hardware security module (HSM) is a hardware appliance that provides secure key storage and cryptographic operations within a tamperresistant hardware module. Client ¶ class CloudHSMClient¶ A lowlevel client representing Amazon CloudHSM This is documentation for AWS CloudHSM ClassicFor more information, see AWS CloudHSM Classic FAQs, the AWS CloudHSM Classic User Guide, and the AWS CloudHSM Classic API Reference. AWS CloudHSM is a cloudbased dedicated, singletenant HSM allowing you to include secure key storage and highperformance crypto operations to your applications on the AWS platform It enables you to securely generate, store, manage, and protect encryption keys in a way that these keys are accessible only by you or authorized users that only.
AWS Cloud HSM is a cloudbased HSM service in the Amazon Web Services The CloudHSM uses FIPS 1402 Level 3 certified Cavium/Marvell HSMs in the backend and is accessible using the PKCS#11 API Custom modules are needed for full EJBCA support of the CloudHSM, and this is supported in the EJBCA Cloud. Now if the file is encrypted using AWS CloudHSM service Is there a provision to load it directly into Snowflake (using COPY INTO) by defining the private keys in the External Stage ?. For information about the current version of AWS CloudHSM, see AWS CloudHSM, the AWS CloudHSM User Guide, and the AWS CloudHSM API Reference Modifies the certificate used by the client This action can potentially start a workflow to install the new certificate on the client's HSMs.
CloudHSM is delivered via singletenant access to a dedicated highly available cluster With KMS, you have the option of creating your own encryption keys or letting AWS do that for you CloudHSM works only with keys that you create This gives you greater control as AWS has no access to the keys that you generate. AWS CloudHSM helps meet corporate, contractual and regulatory compliance requirements for data security by using dedicated HSM appliances within the AWS cloud A hardware security module (HSM) is a hardware appliance that provides secure key storage and cryptographic operations within a tamperresistant hardware module. AWS CloudHSM AWS CloudHSM is a cloudbased hardware security module (HSM) designed for security applications It enables users to generate and use encryption keys on the AWS Cloud, deposit SSL or TLS processing for web servers, protect generated keys in AWS KMS by FIPS 1402 validated cryptographic modules, encrypt and decrypt data on the symmetric and asymmetric algorit.
AWS CloudHSM is a fully managed service that takes care of administrative, timeconsuming tasks such as backups, software updates, hardware provisioning, and high availability by automating these tasks However, AWS does not have any access to configure, create, manage, or use your CloudHSM. The AWS CloudHSM is the newer offering from AWS based on Cavium, not to be confused with the SafeNetbased AWS CloudHSM Classic For more information, refer to the AWS CloudHSM User Guide The EJBCA Cloud and AWS CloudHSM integration includes the following and more steps. We are going to use AWS CloudHSM service to keep all code signing certificates secure and perform code signing on our build server Our build server is Windows Server 10, so I installed AWS CloudHSM client there I activated cluster and all commandline utils work as expected I am able to login, add keys, find keys etc.
The AWS CloudHSM service helps you meet corporate, contractual and regulatory compliance requirements for data security by using dedicated Hardware Security Module (HSM) appliances within the AWS cloud. Description CloudHsmCLI is a Python package that provides a command line interface and supporting Python libraries to perform administrative tasks requiring coordination between the AWS CloudHSM service and the customer’s LunaSA HSM Getting Started with CloudHSM See our documentation online for the latest guide to using the CloudHSM service. CloudhsmCreateLunaClient Creates an HSM client * Global Conditions;.
AWS CloudHSM clusters provide high availability and redundancy by distributing cryptographic operations across all hardware security modules (HSMs) in the cluster Backup and restore is the mechanism by which a new HSM in a cluster is synchronized. CloudhsmCreateHapg Creates a highavailability partition group * Global Conditions;. CloudhsmCreateLunaClient Creates an HSM client * Global Conditions;.
Get a personalized view of AWS service health Open the Personal Health Dashboard Current Status Feb 5, 21 PST Amazon Web Services publishes our most uptotheminute information on service availability in the table below. Awscloudhsm>loginHSM CU awscloudhsm>listUsers awscloudhsm>getHSMInfo awscloudhsm>quit Install SSO Connect as usual NOTE The Amazon HSM Java software is supposed to recognize a file named HsmCredentialsproperties on the Java Classpath However, this may not work for some reason. CloudhsmCreateHapg Creates a highavailability partition group * Global Conditions;.
Managing encryption and key management in the AWS Cloud looks like a piece of cake till we understand the different options and its risk profiles AWS Key Management Service (KMS) and AWS CloudHSM are the two options available for handling key management lifecycle process and supporting cryptographic operations. Be sure to check the pricing page for updates prior to use AWS KMS has a $100/month charge for all customermanaged CMKs, including those that you import yourself In the following chart, I’ve calculated annual costs for some regions. Amazon Web Services – Security of AWS CloudHSM Backups Page 1 Introduction Amazon Web Services (AWS) offers two options for securing cryptographic keys in the AWS Cloud AWS Key Management Service (AWS KMS) and AWS CloudHSM AWS KMS is a managed service that uses hardware security modules (HSMs) to protect the security of your encryption keys.
Action Description Resources Conditions ;. What is CloudHSM CloudHSM is one of the many services from Amazon ( AWS ) If you are familar with HSM it is a HSM sitting in the Amazon Data center CloudHSM's are not Virtualized and these are Physical devices sitting in Amazon Data centers(VPC) CloudHSM's are SafeNet Luna provisioned in the AWS VPC What is a HSM ( Hardware Security Module ). AWS CloudHSM is a fully managed service that takes care of administrative, timeconsuming tasks such as backups, software updates, hardware provisioning, and high availability by automating these tasks However, AWS does not have any access to configure, create, manage, or use your CloudHSM.
CloudhsmCreateLunaClient Creates an HSM client * Global Conditions;. Simply put, AWS CloudHSM is a service that can securely generate, store, and manage cryptographic keys Until now there was no really good way to use and manage cryptographic keys in the public cloud itself If you wanted to have a high degree of confidence in your key management, you needed to do it outside of the public cloud. Awscloudhsmjceexamples These sample applications demonstrate how to use the JCE with CloudHSM They show basic functionality, as well as best practices regarding performance.
We are going to use AWS CloudHSM service to keep all code signing certificates secure and perform code signing on our build server Our build server is Windows Server 10, so I installed AWS CloudHSM client there I activated cluster and all commandline utils work as expected I am able to login, add keys, find keys etc. Action Description Resources Conditions ;. CloudHSM is customerowned and managed AWS owns the responsibility of provisioning the HSM in the customer's VPC environment in AWS In AWS CloudHSM, you create and manage HSM clusters, including creating users and setting their permissions You also create the symmetric keys and asymmetric key pairs that the HSM stores.
Complete AWS IAM Reference;. Cryptsoft CloudHSM® encapsulates Cryptsoft's experience in the key management and security market space and can be deployed into almost any environment with the ability to enhance, integrate with, or replace existing standards based or proprietary solutions. CODE Use the following command to update the configuration files for the AWS CloudHSM client and command line tools, specifying the IP address of the HSM in your cluster If you don't know the HSM's IP address, view your cluster in the AWS CloudHSM console.

Security Of Cloud Hsmbackups Aws Architecture Blog

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings

Using Aws Cloudhsm In High Availability Mode
Aws Cloudhsm のギャラリー

Aws Cloudhsm Classic In High Availability Mode Snowflake Blog
Choosing The Right Cloud Hsm Thales Blog
D0 Awsstatic Com Whitepapers Aws Securing Data At Rest With Encryption Pdf
Q Tbn And9gcrbbeaol96hfrlu0ac03nvke7yh9m Igy14d Lreqxnwhhsx Vg Usqp Cau

Aws Launches Cloudhsm App To Bolster Data Security In The Cloud Siliconangle

Aws Cloudhsm
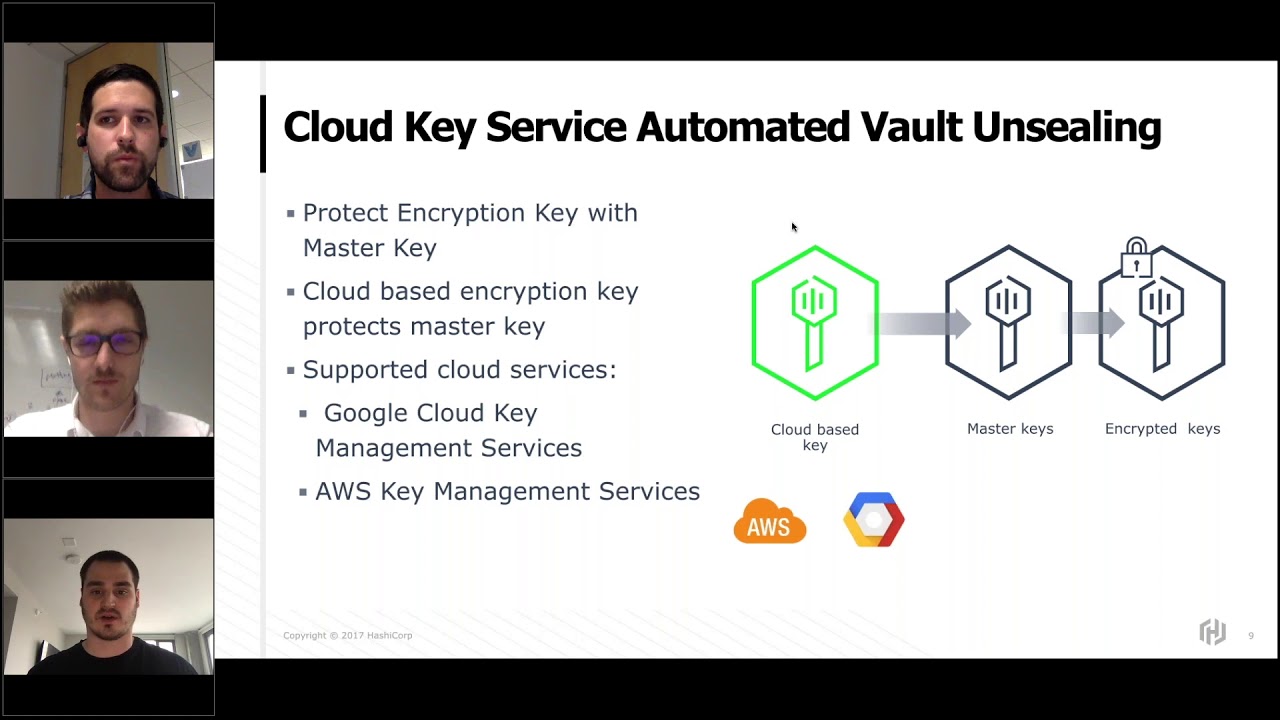
Hashicorp Aws Integrating Cloudhsm With Vault Enterprise Youtube
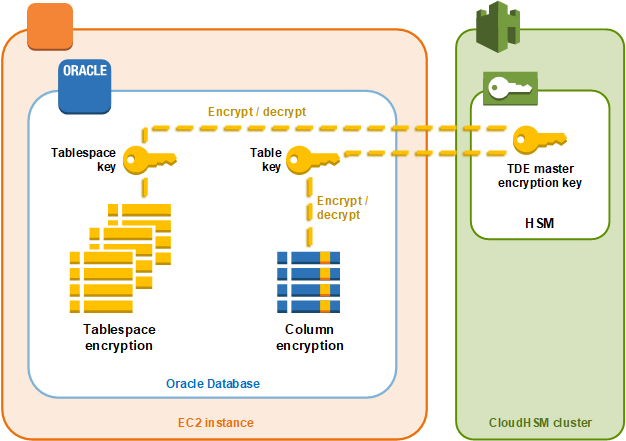
Oracle Database Transparent Data Encryption Tde With Aws Cloudhsm Aws Cloudhsm

Security Iteanz Com

Aws Cloudhsm Aws Security Blog

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Aws Security Blog
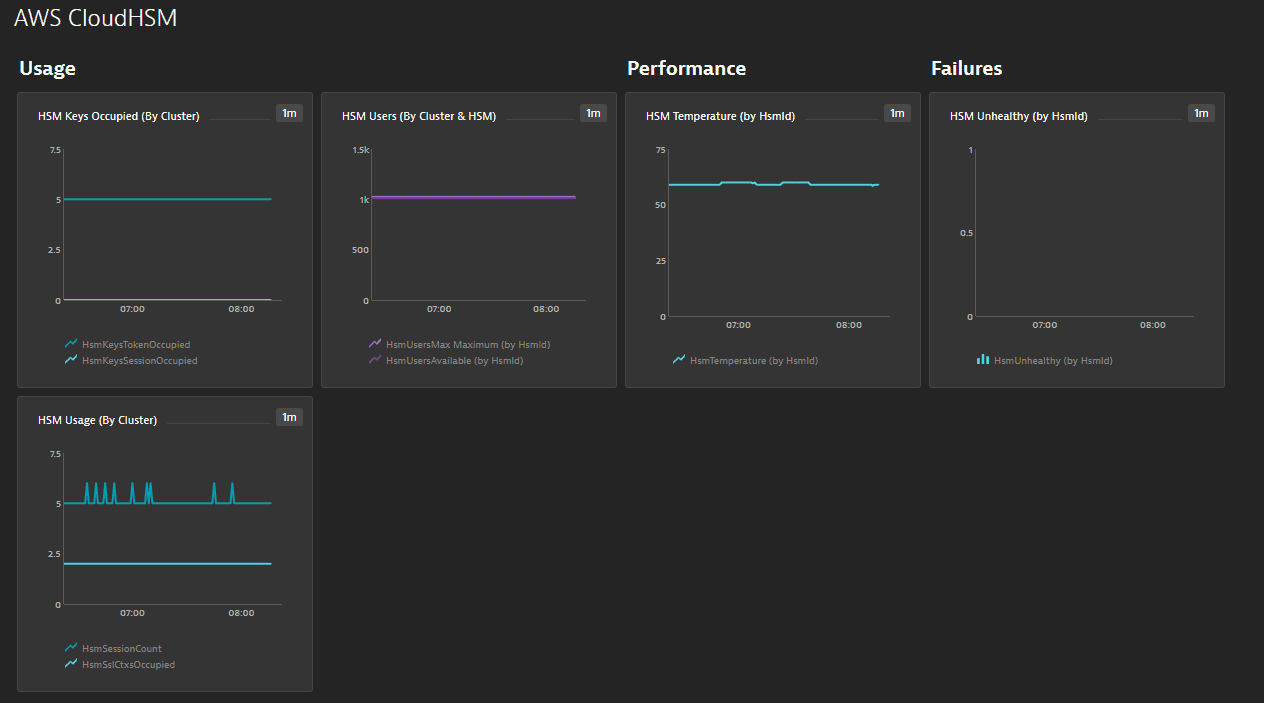
Aws Cloudhsm V2 Dynatrace Help

Integration With Aws Cloudhsm Sso Connect Guide

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Aws Security Blog

How To Remove Single Points Of Failure By Using A High Availability Partition Group In Your Aws Cloudhsm Environment Aws Security Blog

Aws Cloudhsm Digital Cloud Training

How To Migrate Symmetric Exportable Keys From Aws Cloudhsm Classic To Aws Cloudhsm Aws Security Blog

Aws Cloudhsm

Aws Cloudhsm

How To Run Aws Cloudhsm Workloads On Docker Containers Aws Security Blog

Cloudhsm Secure Scalable Key Storage In Aws Aws Online Tech Talks

Aws Kms And Aws Cloudhsm Free Training Notes For The Aws Sysops Administrator Awscertifications

Api Connector For Aws Cloud Hsm V2

Cloudhsm Clusters Aws Certified Security Specialty Exam Guide

Aws Cloudhsm User Guide Hardcover Walmart Com Walmart Com
Docs Aws Amazon Com Cloudhsm Latest Userguide Cloudhsm User Guide Pdf

How To Run Aws Cloudhsm Workloads On Aws Lambda Aws Security Blog

Aws Cloudhsm Dedicated Hardware Security Modu

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings

Bring Your Own Key Byok Setup Process In Appian Cloud Appian 18 3
Docs Aws Amazon Com Cloudhsm Latest Userguide Cloudhsm User Guide Pdf

Aws Cloudhsm Vs Vault What Are The Differences

Cloudhsm Secure Scalable Key Storage In Aws Aws Online Tech Talks

Aws Cloudhsm
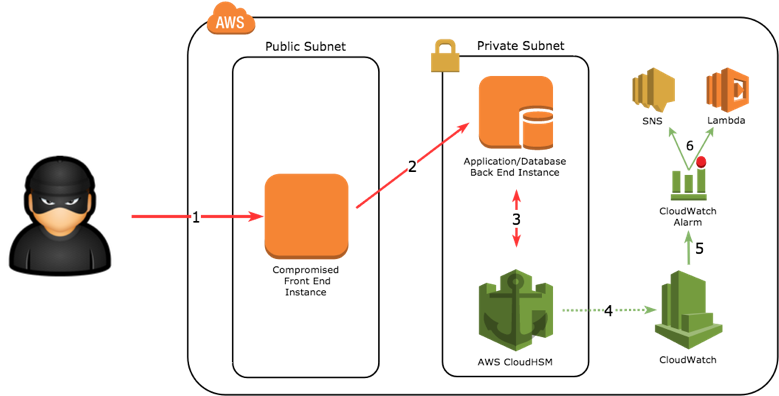
Crypto Anchoring Your Aws Environment Using Cloudhsm Credera
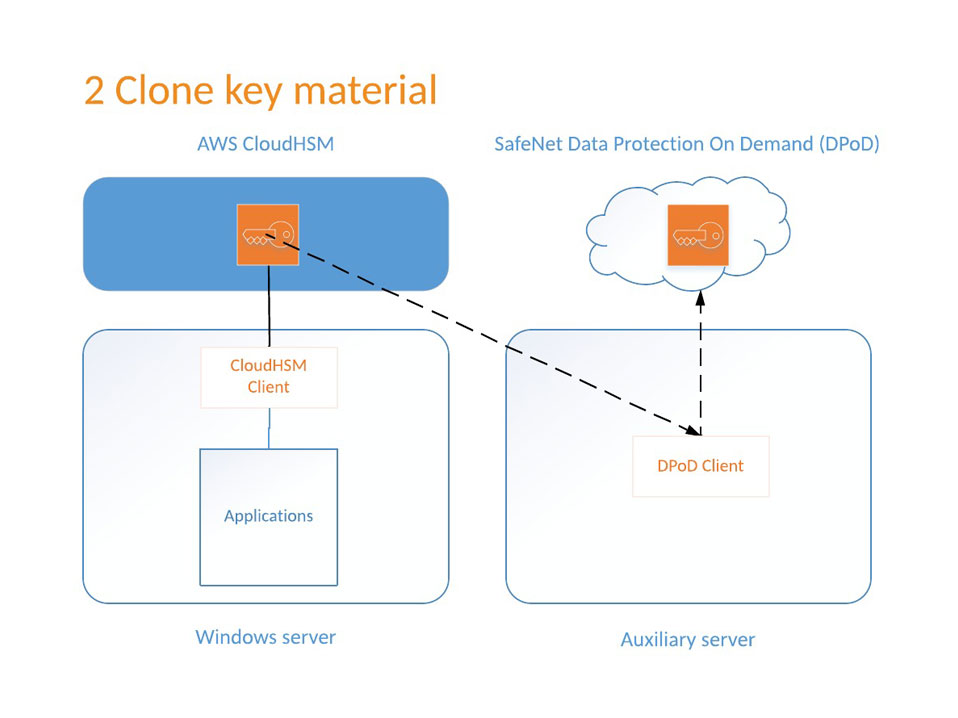
Take Control Of Your Cloudhsm Migration Plan Thales Blog

Overview Aws Kms Aws Cloud Hsm Encryption Consulting

Using Aws Cloudhsm Backed Certificates With Microsoft Internet Information Server Aws Security Blog
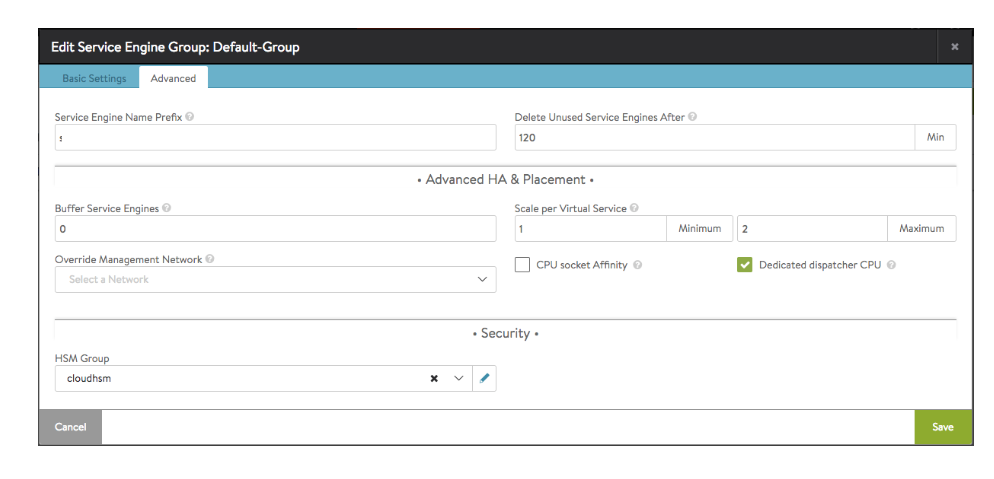
Avi Vantage Integration With Aws Cloudhsm V2

Features Aws Cloudhsm Amazon Web Services Aws
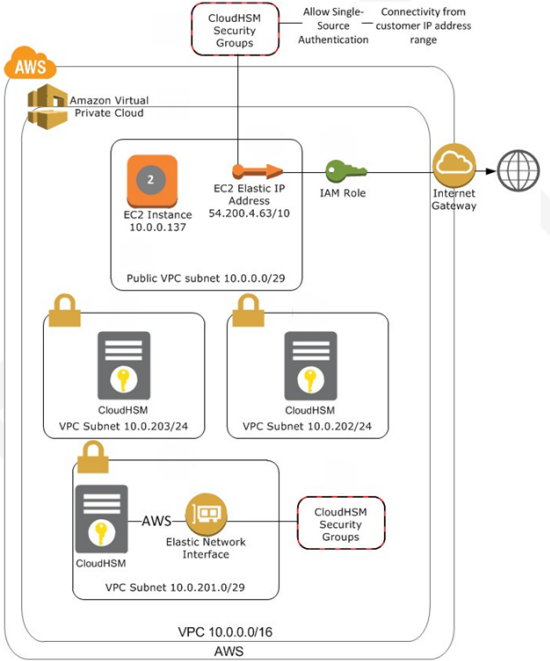
Aws Cloudhsm Update Aws News Blog
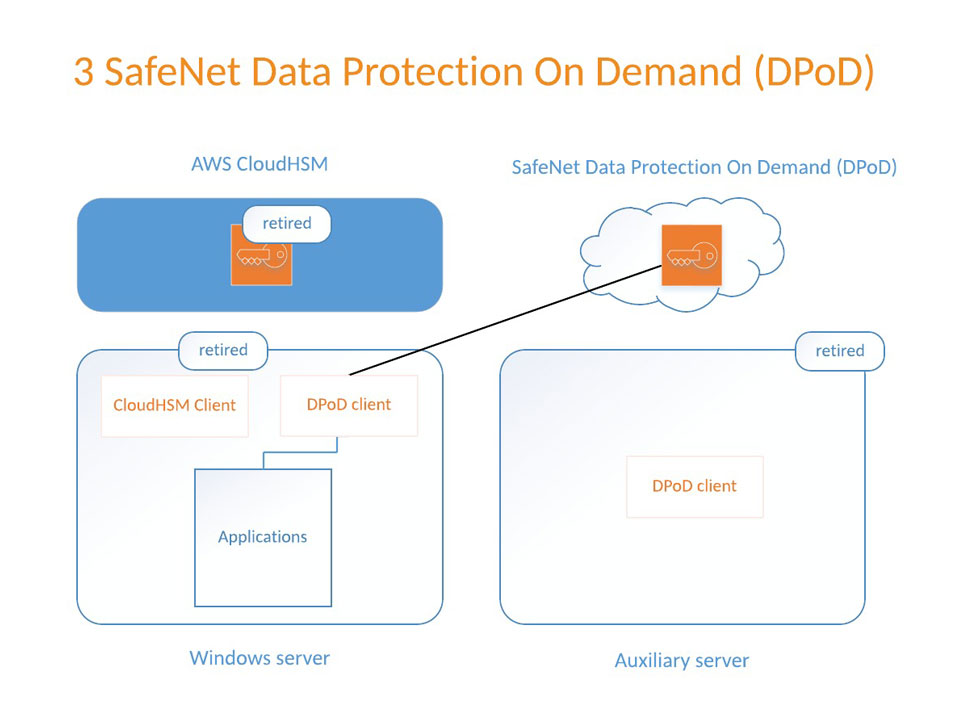
Take Control Of Your Cloudhsm Migration Plan Security Boulevard

Aws Cloudhsm The Modern Logic Group

Grata Software Aws Cloudhsm Is A Cloud Based Hardware Facebook
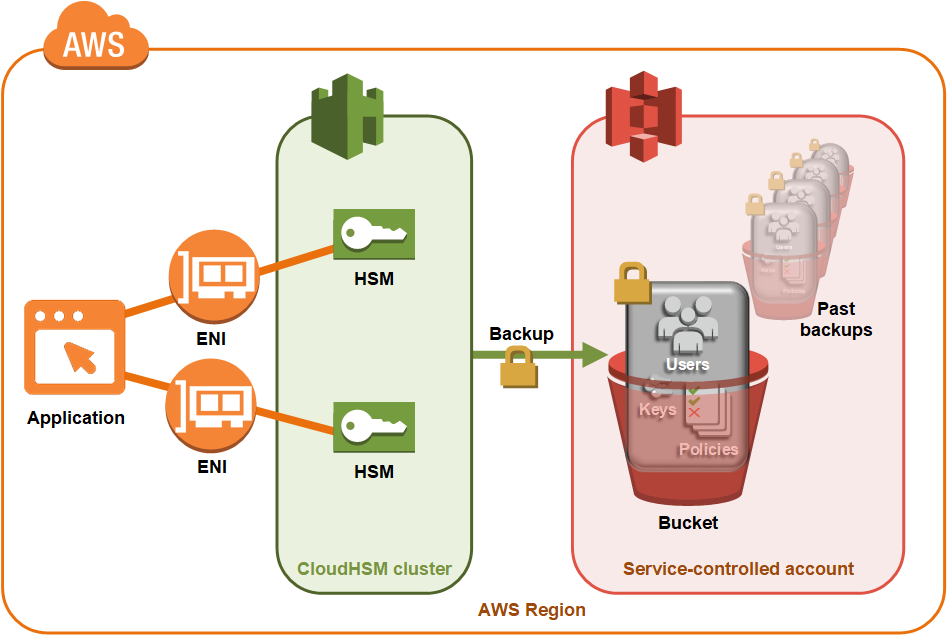
Aws Cloudhsm Cluster Backups Aws Cloudhsm

Aws Cloudhsm Getting Started Guide By Amazon Web Services

Demystifying Public Cloud Security How Public Can Be Made Very Private

Aws Cloudhsm

Aws Cloudhsm Reviews 21 Details Pricing Features G2

What Is Aws Hsm Aws Cloudhsm Tutorial Links

How To Lower Costs By Automatically Deleting And Recreating Hsms Aws Security Blog

Going All In On Aws Cloud Security Boulevard

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Aws Security Blog

Features Aws Cloudhsm Amazon Web Services Aws

Aws Cloudhsm

Using Aws Cloudhsm Backed Certificates With Microsoft Internet Information Server Aws Security Blog
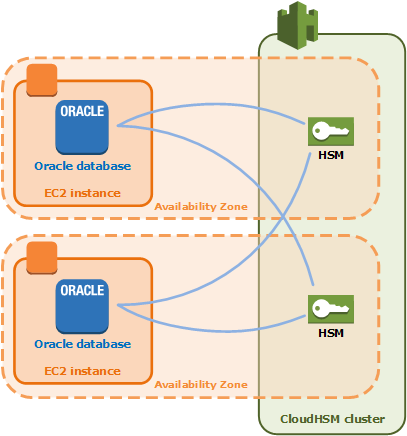
Aws Cloudhsm Clusters Aws Cloudhsm

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Aws Security Blog

New Kaleido Cloudhsm Signer Services Store Manage Use Cryptographic Keys With Azure Aws Hashicorp Vault

Sun Coree Db

Apn Tv Achieving Security Goals With Aws Cloudhsm Sdd333

Amazon Cloudhsm Aims To Ease Security Worries Informationweek
Q Tbn And9gcrejirfjqubbxazmdeqo3z0prq3tjwvzfwo Nvp0ntb1sbxx7ln Usqp Cau

How To Migrate A Digital Signing Workload To Aws Cloudhsm Terabitweb Blog

Understanding Aws Cloudhsm Cluster Synchronization Aws Security Blog
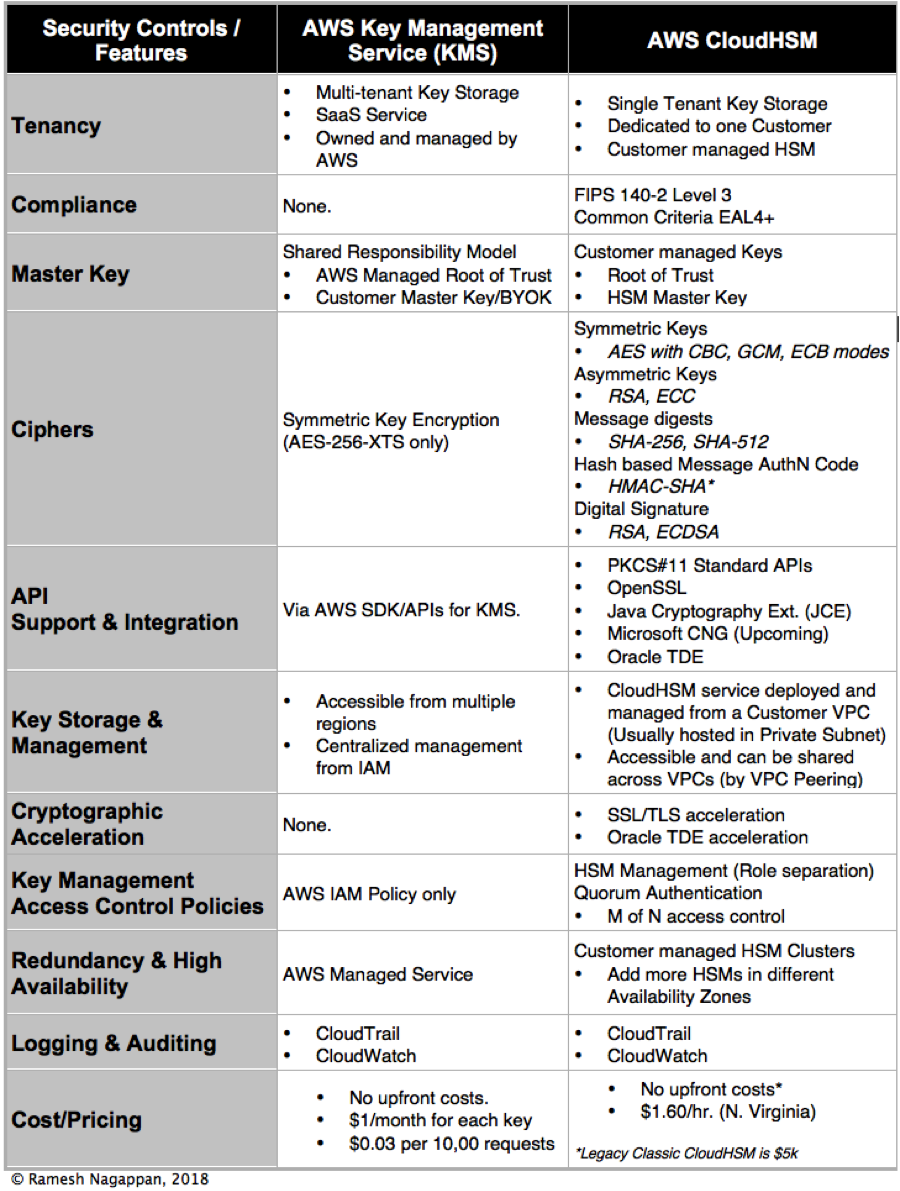
Encryption And Key Management In Aws Comparing Kms Vs Cloudhsm Web Security Patterns

Aws Cloudhsm Aws Security Blog

How To Byok Bring Your Own Key To Aws Kms For Less Than 15 00 A Year Using Aws Cloudhsm Terabitweb Blog
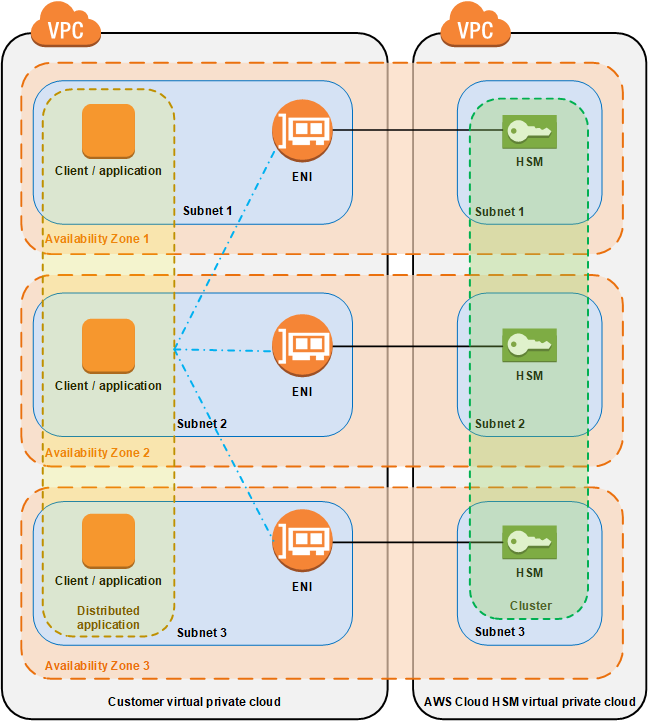
Aws Cloudhsm Clusters Aws Cloudhsm
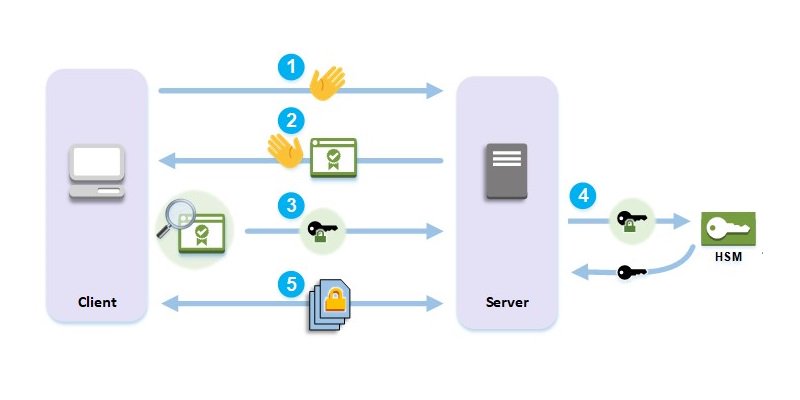
Amazon Web Services Use This New Aws Cloudhsm Tutorial To Improve Your Web Server S Security With Ssl Tls Offload T Co 2ynadzqtmg T Co Cqnlvar31l
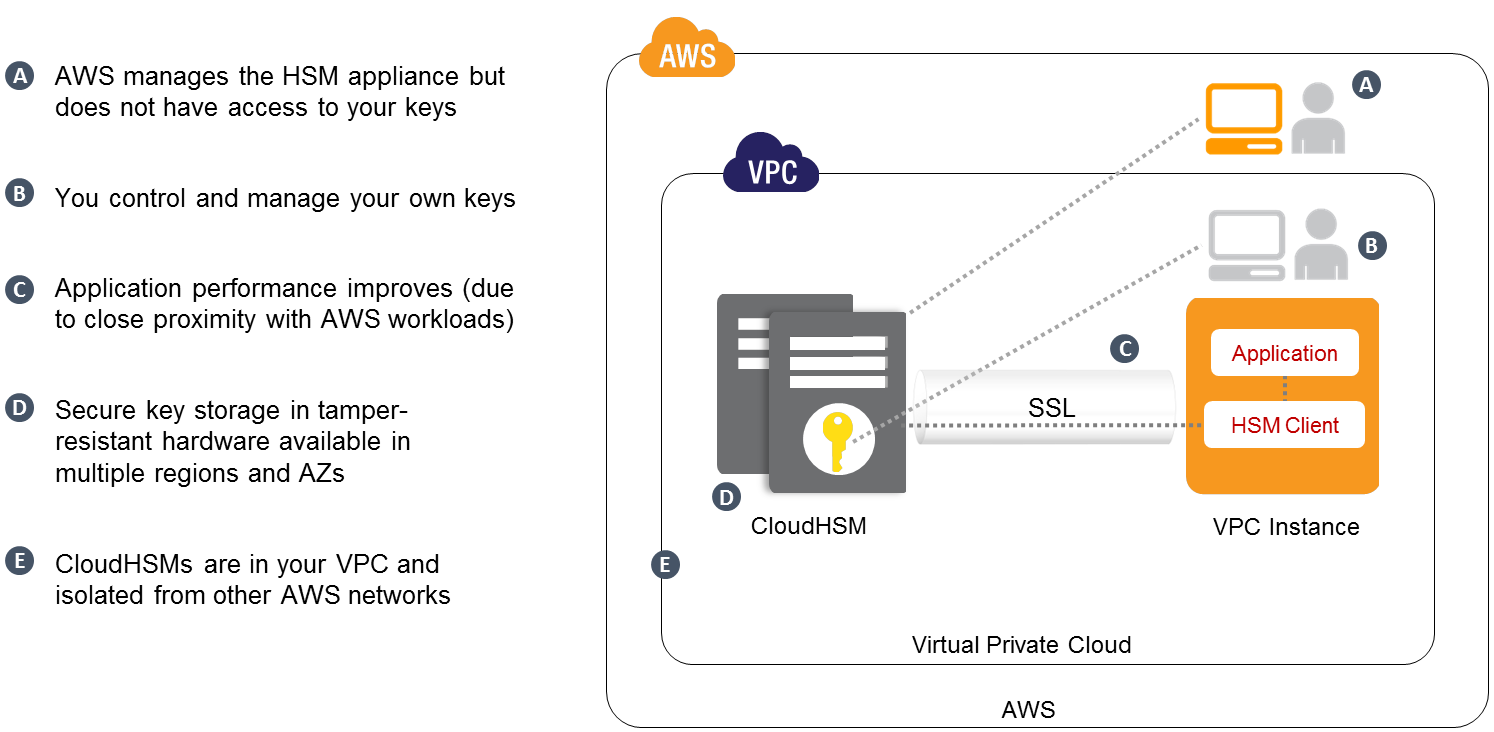
Amazon Web Services Launches Cloudhsm A Dedicated Hardware Security Appliance For Managing Cryptographic Keys Techcrunch

Aws Cloudhsm User Guide

Aws Cloudhsm Classic In High Availability Mode Snowflake Blog

Aws Cloudhsm Another Amazing Service By Amazon Web Services Cloudreviews Cloud Hosting Cloud Storage Managed Hosting News Industry Updates Blog
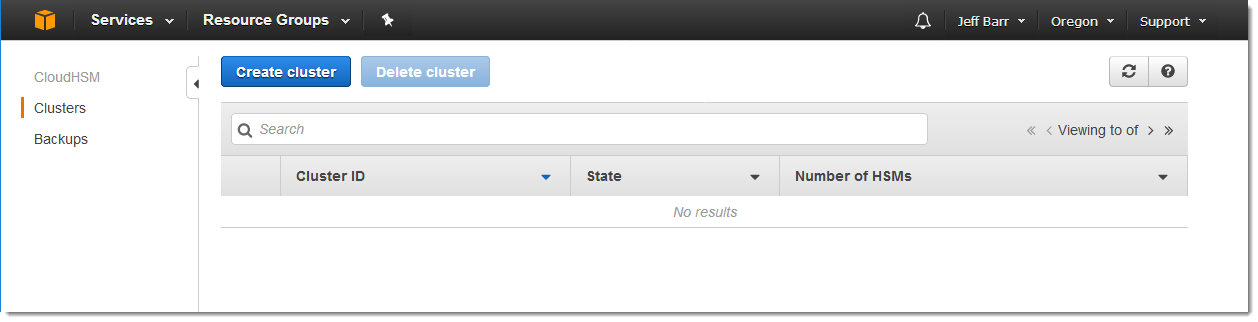
Aws Cloudhsm Update Cost Effective Hardware Key Management At Cloud Scale For Sensitive Regulated Workloads Aws News Blog

How To Update Aws Cloudhsm Devices And Client Instances To The Software And Firmware Versions Supported By Aws Aws Security Blog

Aws Cloudhsm Digital Cloud Training

Cloudhsm Secure Scalable Key Storage In Aws Aws Online Tech Talks

Migrating From A Aws Cloudhsm Classic Partition

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Aws Security Blog

Bring Your Own Key Byok Setup Process In Appian Cloud Appian 18 3

Aws Black Belt Online Seminar Aws Cloudhsm Youtube

How To Clone An Aws Cloudhsm Cluster Across Regions Aws Security Blog

Aws Cloudhsm Reviews 21 Details Pricing Features G2
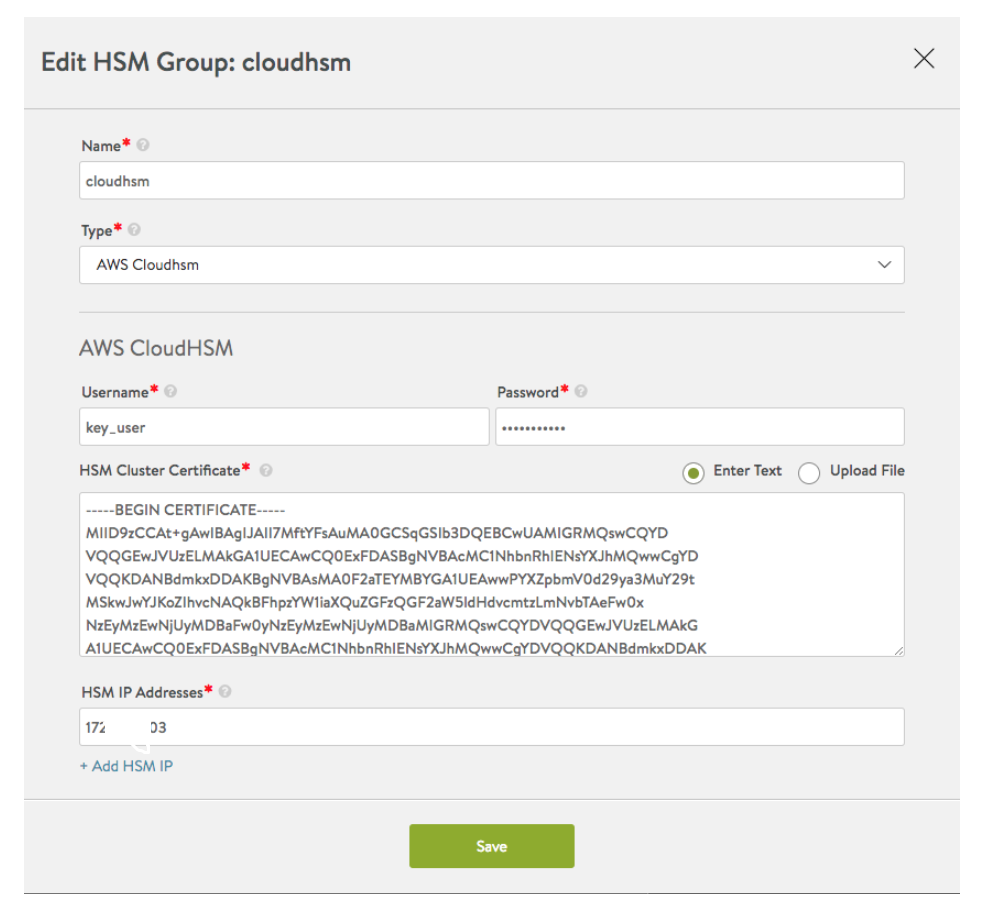
Avi Vantage Integration With Aws Cloudhsm V2

Understanding Aws Cloudhsm Cluster Synchronization Aws Security Blog
Cloudhsm Secure Scalable Key Storage In Aws 17 Aws Online Tech Talks Youtube

Securing Data At Rest With Encryption

Migrating From A Aws Cloudhsm Classic Partition

Aws Cloudhsm Aws Security Blog

Aws Cloudhsm Classic User Guide By Amazon Web Services
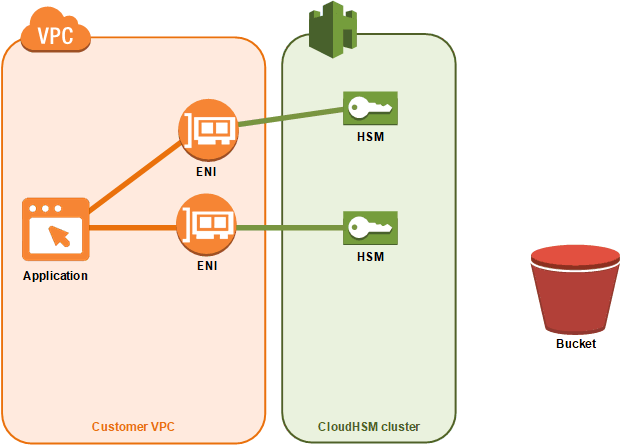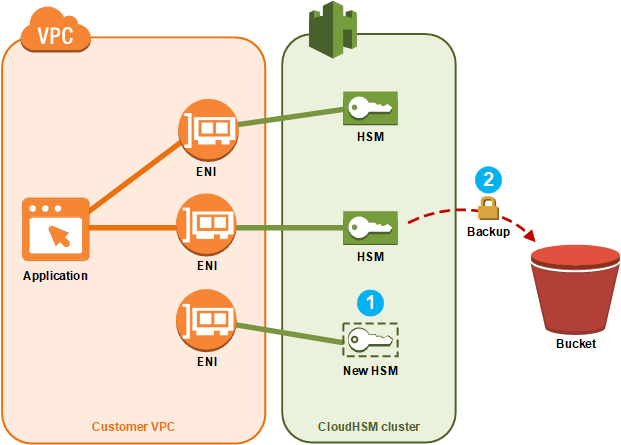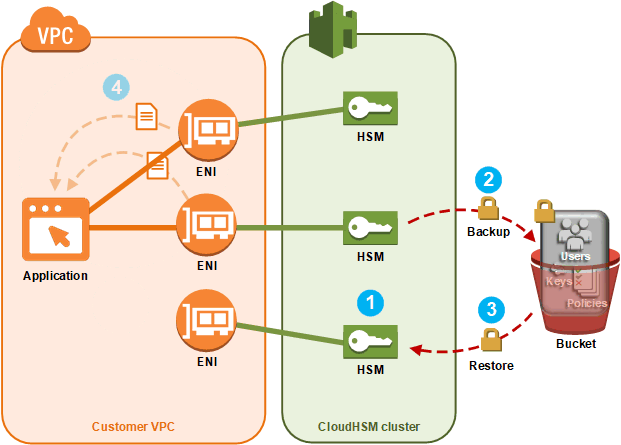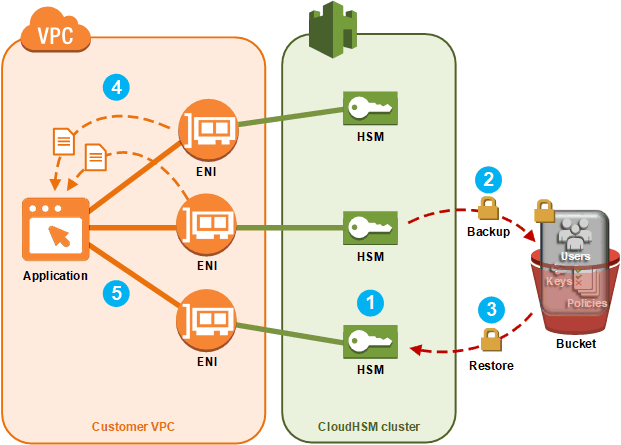
Adding Or Removing Hsms In An Aws Cloudhsm Cluster Aws Cloudhsm

Aws Cloudhsm Vs Google Cloud Endpoints What Are The Differences
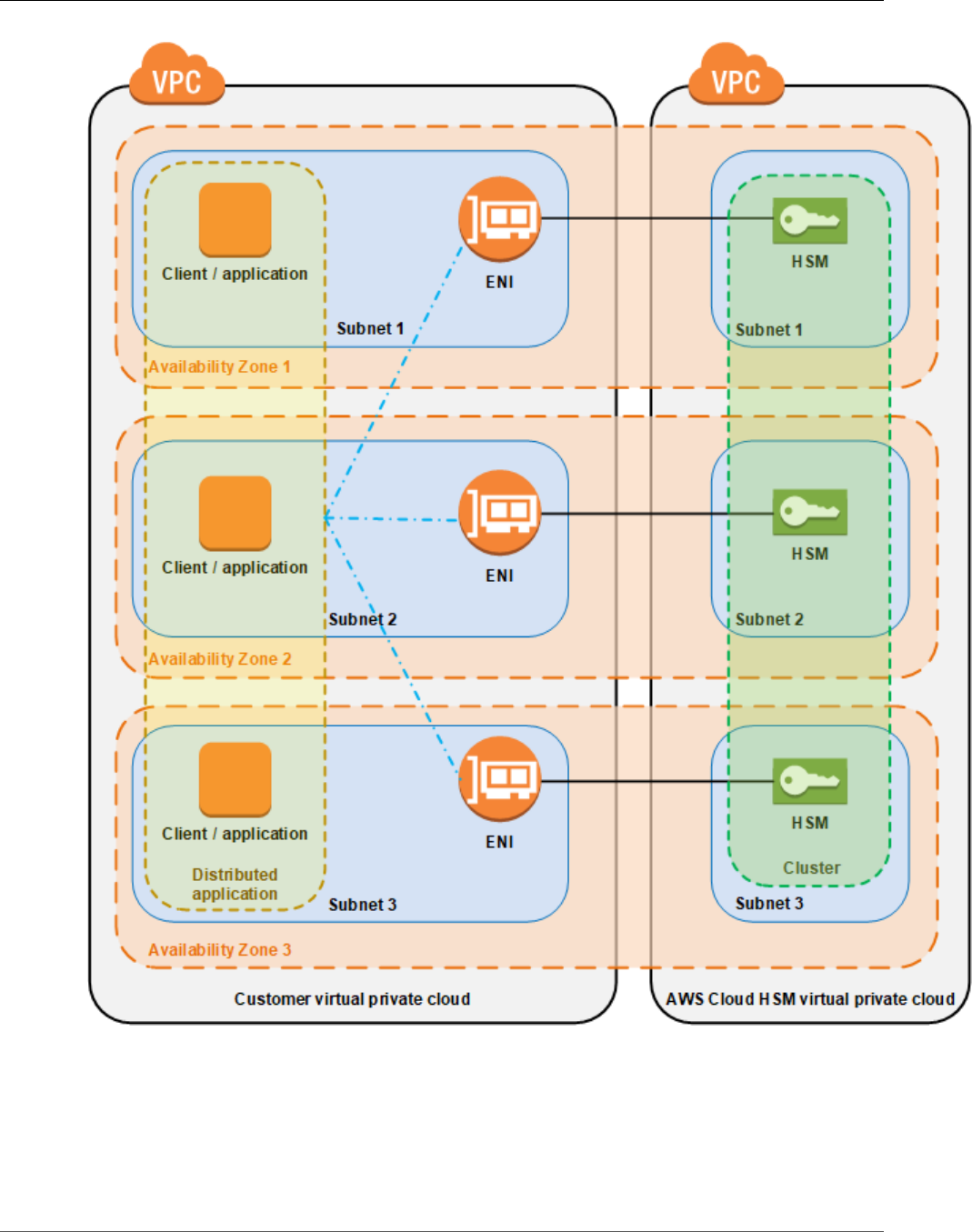
Aws Cloudhsm User Guide
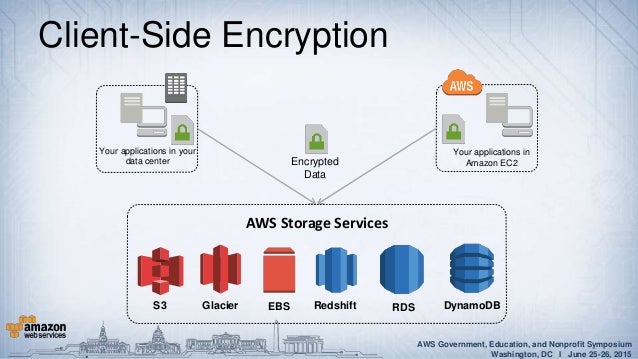
Protecting Your Data With Aws Kms And Aws Cloudhsm

Why Would You Deploy Your Pki In The Cloud Primekey
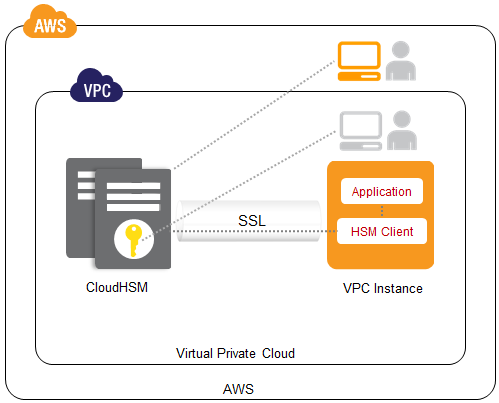
Aws Cloudhsm Secure Key Storage And Cryptographic Operations Aws News Blog

Deep Dive Aws Cloudhsm Classic
Q Tbn And9gcrouf2zzrjjqwghhowvp8i2rnvhlhhn9viqeu0mu0nsto559jn5 Usqp Cau
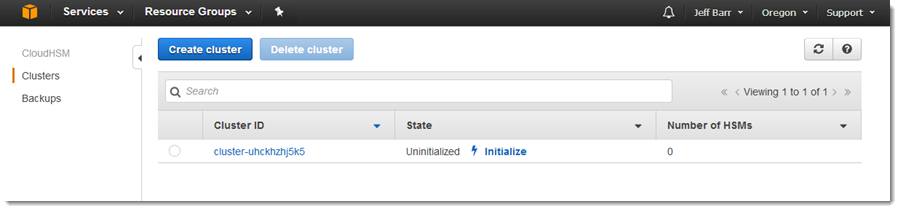
Aws Cloudhsm Update Cost Effective Hardware Key Management At Cloud Scale For Sensitive Regulated Workloads Aws News Blog




